From the moment you open your Android device to access the online world, your data is tracked by several parties. From relatively benign entities that keep track of your online presence to sell you ads and services to hackers who want to steal your personal data, your data is under constant attack. The best Android phones offer several layers of protection to secure your data on the device, but they can't do anything about the data passed on the internet.
Since it's impossible to stop someone from accessing your online data, the next best thing to do is to convert your data into a string of gibberish that no one can understand. That's why encryption has become the backbone of online communication. To ensure your communication is not intercepted and read by hackers, government agencies, or malicious parties, your means of communication must use end-to-end encryption.
But what is end-to-end encryption, and why should you care? In this guide, we take an in-depth look at end-to-end encryption and teach you everything about it.
What is encryption?
Before we understand end-to-end encryption, let us first understand the basics. Encryption converts data into a scrambled mess, so only authorized parties can access it. For example, let's say you want to send a message to your friend. The message isn't directly delivered from your device to your friend's device. Instead, it travels the online infrastructure, including your ISP (internet service provider), the messaging app server, and all the parties in-between to reach its destination.
To ensure that no one can read your message while in transit, your messaging service uses mathematical cipher algorithms to encrypt the data, which converts your plain-text message into cipher text. The cipher text is an incomprehensible string of text which is essentially useless. The only way to convert this cipher text into the original message is by using the decryption key. It means that even if a hacker accesses your message in transit, they cannot read it as they don't have access to the decryption key.
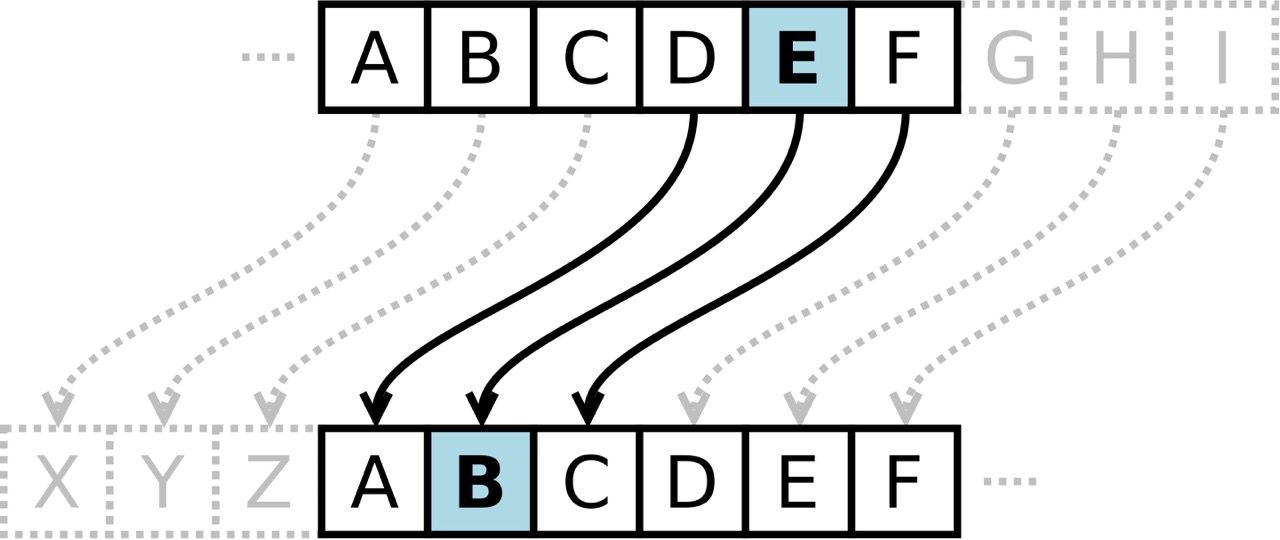
One of the earliest records of cipher text is Caesar's cipher, created by Julius Caesar. It is a shift cipher that uses a simple substitution algorithm to obfuscate his messages. Each letter of the message was substituted with another letter down the alphabet by a fixed number. For example, if one uses the substitution algorithm of shift 3, the letter A would become D, B would become E, and so on.
In the age of computers that can compute millions of bits of data in seconds, such a simple cipher has been replaced with complicated mathematical algorithms, but the basic principle remains the same. Several types of encryption algorithms are used today, each with its own benefits and challenges. In this guide, we focus on end-to-end encryption or E2EE.
End-to-end encryption's public and private keys
E2EE is the type of encryption where a message is encrypted at the sender's end and decrypted on the receiver's end. The message remains encrypted at all points during the transit, so even if someone intercepts it during transmission, they can't read its contents.
The term end-to-end refers to this same fact. The encryption and decryption of the messages happen only at the endpoints, the sender and the receiver ends. The message is not encrypted or decrypted at any point in transit. Even the server relaying and storing your message cannot decipher and read your messages.
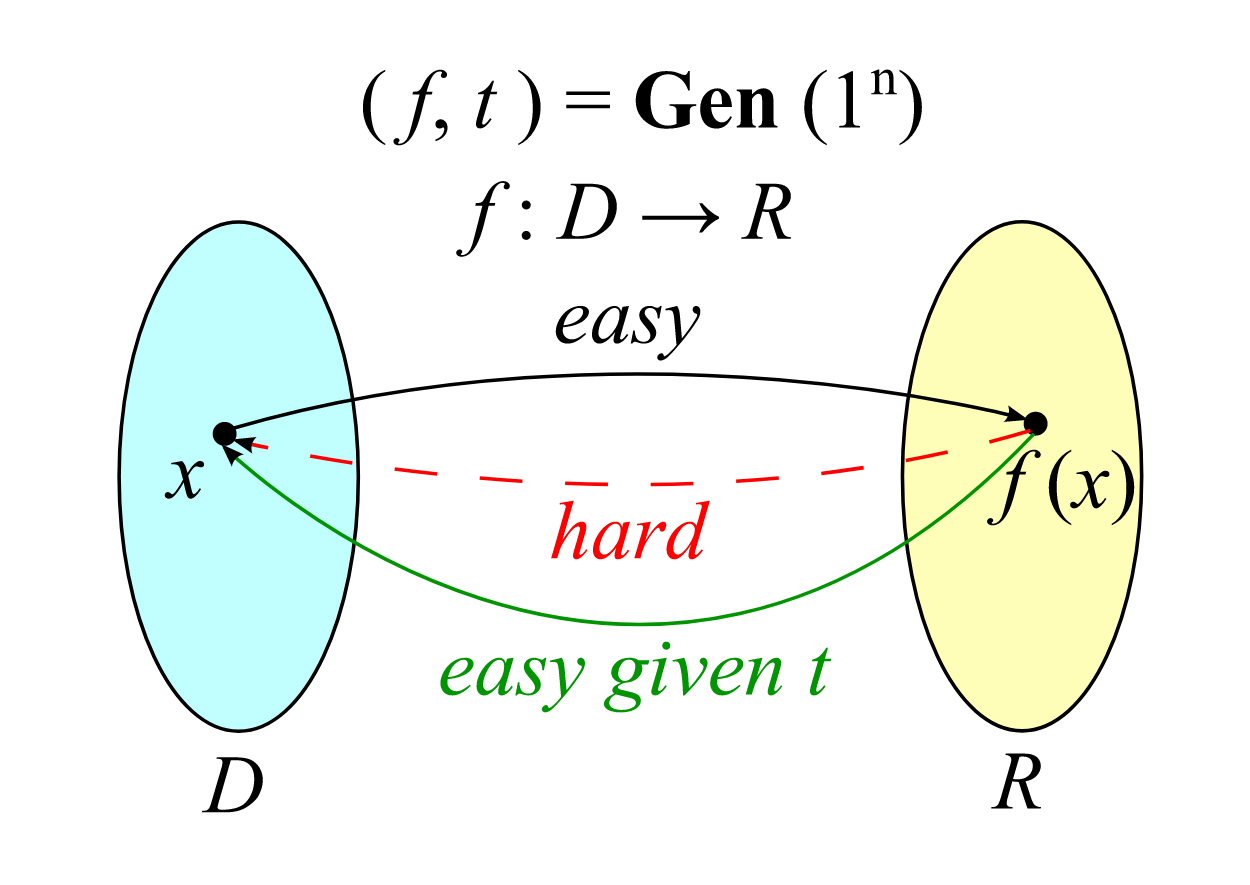
End-to-end encryption uses asymmetric public key encryption, where both parties have two keys. When we say key, we mean the mathematical algorithm used to decrypt or encrypt a message. One of the keys is the public key that anyone can access, while the other is the private key that is not shared with anyone else. The public key is used to encode a message, and this encoded message can only be decoded using its corresponding private key.
When somebody sends you an encrypted message, their app uses your public key to encrypt the message. The encrypted message is sent over the internet. However, the public key can't be used to translate the message into its original form. To do that, you need your private key. This is possible because the public key and private key are linked in a way that is nearly impossible to figure out when looking at the public key alone.
The fancy math behind end-to-end encryption
As it exists today, technology can't figure out someone's private key. The trick to the process is this: Figuring out someone's private key is borderline impossible using current technology. Generating the two keys involves using a one-way function. This one-way function is a calculation that is easy for a computer to perform but takes a huge amount of computing power to reverse. Reversing the function becomes nearly impossible when these functions are performed on large enough numbers, such as a 64-digit private key.
One simple type of one-way function is to take a number, square that number, divide it by the product of two prime numbers, and take the remainder. Knowing the two prime numbers makes it easy to reverse the function and figure out the original number. However, figuring out the original number without the prime numbers requires brute force. If the two prime numbers are large enough, no computer in the world has the computational power to brute force the answer.
Finding someone else's private key makes it easy to decrypt a message. Many apps frequently switch users' private and public keys to mitigate this issue. Discovering a user's private key for one of these apps only decodes a few messages. The rest remain encrypted and unintelligible.
Benefits and drawbacks of end-to-end encryption
As we said, every type of encryption has its own benefits and challenges. It's the same with end-to-end encryption. That said, in terms of messaging services, the benefits outweigh the challenges. Let's have a quick look:
Benefits of E2EE
The primary benefit of E2EE is that the data is only decrypted and encrypted at the endpoints, making it impossible for hackers or government agencies to access your messages. It makes the service perfect for journalists, activists, and the general population that don't want their conversation to come into the public eye. Here are the other benefits of end-to-end encryption:
- Privacy: Your data is always encrypted, so you can be sure that your data will always be private.
- Security: The government cannot force service providers to divulge your private communications as no one has access to decrypted chats other than communicating parties.
- Integrity: E2EE also ensures you can trust that the data you receive is from a secure sender, as no one in transit can manipulate the data to feed you false information.
- Secure remote work: Since the COVID-19 pandemic, a portion of the workforce has moved to work from home. For companies, E2EE ensures that workers can access companies' tools securely.
Drawbacks of end-to-end encryption
Now that you know about the benefits of end-to-end encryption, let's check out some of its drawbacks.
- Uses more resources: End-to-end encryption uses more resources to encrypt and decrypt data, which makes it not an ideal candidate for large data transfers.
- No content monitoring: Since the messages cannot be monitored, nefarious parties can use E2EE to communicate without getting caught.
- No lost data recovery: If you lose your device or data, there's no way to recover it, as no one else has your decrypted data.
- Does not hide communication log: While E2EE secures your messages, it cannot hide that data is being transferred between two partiers. So while no one can read your messages, they can find with whom and when you are communicating.
Which communication apps use end-to-end encryption?
It's one thing to know what end-to-end encryption is. But that information is hardly useful if you don't know which apps use it. The following apps have end-to-end encryption either as an option or enabled by default.
Signal
Signal is a unique messaging app. And it's not because of its features. It's because of its underlying philosophy. The free app, which has end-to-end encryption for all its messages, was made by the nonprofit Signal Foundation. This foundation has the stated goal of developing open source privacy technology for communications. Because of this, Signal is an open source app, as is its underlying encryption protocol called the Signal Protocol. This protocol has been used by multiple other apps, including Meta's WhatsApp, Google's now-defunct Allo, and Microsoft's Skype.
Threema
Threema is another messaging app with end-to-end encryption enabled for all its messages. However, the philosophy driving Threema's creators, the Swiss company Threema GmbH, couldn't be more different from Signal's. Threema is a proprietary app, so the exact way it functions isn't open to the public. It's also a paid app, meaning you must fork out $5.00 to use it. Threema also offers a self-hosted version of its software that companies can install on their servers if they need extra security.
WhatsApp is the world's most popular messaging and video chat app, with about two billion monthly active users across the globe. While it's decently popular in the United States, the residents of some countries use it as their primary messaging app almost exclusively. For example, 96% of South Africans use WhatsApp, as do 93% of Argentinians and 91% of Brazilians.
WhatsApp uses the same end-to-end encryption protocol as Signal. The app automatically enables this encryption for its messaging and business messaging functions, and you can turn on end-to-end encryption for your message backups.
Telegram
Unlike Signal, Threema, and WhatsApp, Telegram doesn't automatically enable end-to-end encryption for its users. However, secret chats use end-to-end encryption. This type of chat can only be used when the recipient is online. Telegram has other privacy-conscious features, such as self-destruct timers that erase secret messages and a setting that automatically deletes your account after a set period of inactivity.
Facebook Messenger
Since Meta owns Facebook and WhatsApp, it shouldn't be surprising that Facebook Messenger has end-to-end encryption. However, unlike WhatsApp, Facebook's end-to-end encryption capability doesn't apply to all messages. To enable end-to-end encryption in Facebook Messenger, click the "i" button in the upper-right corner of an existing conversation, then turn on secret conversations. Secret conversations also have the option to delete messages automatically after a set period of time.
Wire
Wire has a wider range of communications that it can encrypt. Along with messages, Wire can apply end-to-end encryption to its file-sharing, voice calls, video calls, and conference calls with up to 25 other people at once. Wire also has team collaboration capabilities, which are also end-to-end encrypted.
Google Messages
Google's default texting app for Android devices is a recent addition to the list of apps with end-to-end encryption. The chats are automatically end-to-end encrypted if both parties use Google's RCS messaging service.
More ways to protect yourself
Encryption is one way to keep your privacy intact online. Other useful steps involve enabling two-factor authentication, opting out of data collection when possible, and opting out of targeted advertising. Our article about how to enhance privacy on your Android phone is a good place to start when it comes to learning what you can do to keep your data safe, or at least as safe as possible, in this modern world.


.png)