latest

EarSpy can eavesdrop on your phone conversations using motion sensors
Researchers from five American colleges have collectively developed this side-channel attack
Read update
Mobile security is kind of like a highway: new potholes form every day and its throughput capabilities are highly dependent on the drivers taking care not to cause a pile-up. Whether these crashes are caused by researchers sniffing out a new vulnerability, players down the security chain not doing their part, or worse, all of it's happening day in, day out. A group of researchers from some of America's most reputed academic institutions have now developed an attack named EarSpy, designed to capture what users say through curiously crafty means.

Apple ain't afraid of no PACMAN as it downplays M1 chip vulnerability
It's not known if this exploit could work against other Arm chips
Apple has wrapped up a big week with WWDC 2022 done and dusted and a new MacBook Air announced with a new M2 chip. But while the company may have had confetti and bugspray on its agenda, it also downplayed a new vulnerability on its M1 chip as uncovered by MIT's Computer Science & Artificial Intelligence Laboratory this week.

Motorola phones at risk of hacking with chip-level vulnerability
At the center of attention is a chipset from Unisoc
Chinese chipmaker Unisoc has been able to seize upon opportunities in the global chip shortage crisis. As Taiwanese cohort MediaTek has been able to ascend with more upscale products, so has Unisoc, taking the former's place in more budget phones. But such a rise is due stricter scrutiny: we've seen one of the company's older chips marked as a threat vector, putting owners of a number of budget phones at risk with only some prospect of a patch. Now, we're learning about another vulnerability that's explicitly affecting a Unisoc chip in three Motorola devices.

Huawei AppGallery vulnerability allows paid apps to be downloaded for free
Don't expect this hole to remain open for long
Following the US ban, Huawei lost access to Google services. As a result, it had to invest more resources into its own software, Huawei Mobile Services (HMS), for use on its smartphones. Part of that is the Huawei AppGallery, the company’s alternative to the Google Play Store. Now, the whole point of an app store is to distribute software, and that includes collecting money for paid titles. Unfortunately for Huawei, a flaw seems to allow users to download paid apps for free.

Linux Dirty Pipe kernel bug exposes Android to potential malware vector
Get ready to clean those dirty pipes
If Android were a car engine, and you popped the hood and poked around a bit, you'd find the label "Linux" etched on the engine block. The open-source operating system provides the starting point that Android's built on top of, but sharing code also means sharing vulnerabilities. Now a newly discovered Linux kernel bug is raising concerns for the security of Android devices, as it leaves a door open for malware intrusion.
Beijing's app for Olympic athletes and visitors looks like a free data buffet for hackers
Thousands at risk of having personal data exposed
There are privacy concerns for the thousands of foreigners in Beijing for the 2022 Winter Olympics after Canadian research group Citizen Lab revealed vulnerabilities in an app that handles sensitive health information and is required by the Chinese government for anyone involved with the games.
Vulnerability in recent MediaTek chips could allow apps to eavesdrop on you, but it's been fixed
The exploit was not observed in the wild
Today, Check Point Research has discovered a vulnerability in the AI and audio processing components for recent MediaTek chipsets, which could allow what is called a local privilege escalation attack from a third-party application. In short, that means that an app loaded with the right code could get access to AI and audio-related information it shouldn’t have — theoretically even eavesdropping on device owners. Thankfully, the issue was never caught being exploited in the wild, and MediaTek has fixed the related vulnerabilities as of October.

Your phone (and everything else) might be vulnerable to 'frag' attacks over WiFi
And your laptop, and your smart bulb, and just about anything that uses WiFi
Just days after we heard about the Qualcomm vulnerability that could let hackers listen to your calls, a security researcher has brought to light several Wi-Fi vulnerabilities, some of which even relate to the Wi-Fi standard itself. The new findings affect not just your phones, tablets, and laptops but just about any device that uses the technology that wirelessly connects to the internet.
Samsung phones already protected against modem vulnerability that lets hackers listen to your calls
The Qualcomm issue affects an estimated 40% of Android phones
Read update
Google and other Android manufacturers try to keep on top of the hardware and software security, at varying degrees of intensity. But a vulnerability in widely-used Qualcomm SoCs disclosed by Check Point Research today was particularly alarming. It could theoretically allow a malicious app to patch the software for Qualcomm's MSM modem chips, giving it access to call and text history or even the ability to record conversations. Thankfully, most Samsung phones have already received a patch fixing the problem, and the rest is in for an update next month.

SHAREit app with over a billion installs suffers security vulnerability days before US ban
The executive order banning the app on Friday doesn't appear to have been reversed
The popular SHAREit app isn't just set to be banned in the US in the next three days; it was also apparently vulnerable to a (slightly convoluted) attack. The technical details are a bit of a slog, but in short, the app could indirectly allow for the execution of arbitrary code remotely, read or overwrite the app's local files, or even allow for third-party APKs to be installed. Developers of the app, which claims over a billion installs at the Play Store, were notified of the vulnerability three months ago, but according to Trend Micro, they haven't done anything to address it.

Yesterday, Chrome was patched to fix a major vulnerability discovered by researchers, which was actively exploited in the wild. Precise details aren't known right now, but an update rolled out for Chrome yesterday, and you'd be wise to install it as soon as you can.

Twitter finally gets around to patching Android app security hole... 22 months later
An attempt to show it cares about security
Twitter has patched its app from a vulnerability within Android that could let a malicious app siphon users' private date — including their direct messages — while bypassing system permissions. Every Twitter for Android user was notified about the security hole which affects users on versions 8 Oreo and 9 Pie.

WhatsApp fixes issue that exposed some users' phone numbers to search engines
Probably also not a good idea to leave phone numbers unencrypted in the URL
Facebook went on a whack-a-mole expedition patching a security vulnerability that exposed thousands of WhatsApp users' phone numbers with a fairly simple Google search. The Indian researcher who found this loophole is also crying foul for not being able to receive a bounty for his bug find.

MediaTek security vulnerability allowed root access on devices from Nokia, Amazon, BLU, Sony, ZTE, and others
Some OEMs have patched it already
Security vulnerabilities are unfortunately extremely common in smartphones, given the complexity and varying codebases of most devices. That's why Google has been releasing monthly security patches for years, and if you needed another reason for why those updates are so important, the March 2020 release fixes a critical flaw on many MediaTek devices.

Mozilla has patched a zero-day exploit in late revisions to Firefox 72 and version 68 of the Android web browser. In a security advisory, the company said that it was made aware of "targeted attacks in the wild abusing this flaw."
Read update
- The vulnerability has been patched again. The 2019-10-06 patch level contains the fix, so if your device is affected and shows a notification for an update, you should accept it as soon as possible.
Android security has come a long way in recent years. The promotion of monthly patches has kept many rising threats at bay while Google Play Protect largely bars malware from the Play Store. Despite these achievements, there are still instances where bad actors can exploit Android's code for nefarious purposes. Google's Project Zero team recently reported such an incident, and you may be at risk if you own one of the affected phones.

A research team has publicized about a vulnerability in Bluetooth that may affect nearly every device that supports the wireless communication protocol. Chipmakers were made aware to the so-called Key Negotiation of Bluetooth (KNOB) Attack in November. BlackBerry and Google have announced patches for Android devices.
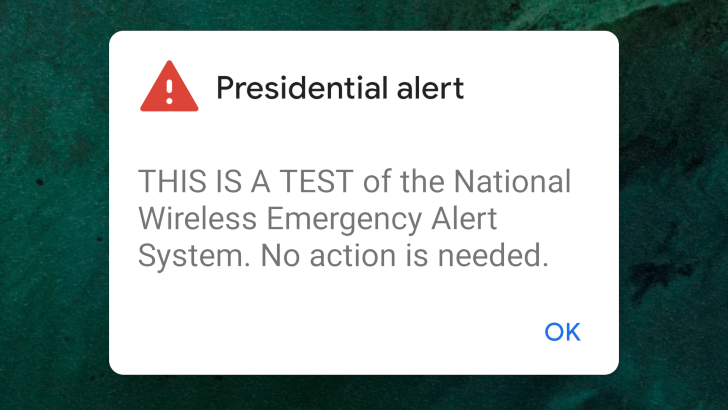
Last year, the United States performed the first public test of the national Wireless Emergency Alert (WEA), an alert system designed to send messages to smartphones, TVs, and other systems simultaneously. The test was specifically for the 'Presidential Alert,' a new category that can't be opted out of (like AMBER alerts). It turns out these types of alerts can be easily spoofed, thanks to various security vulnerabilities with LTE towers.

Firefox developer Mozilla has rolled out an update to the release channel of its browser app for Android that adds an important security fix. The update to version number 67.0.3 patches the critical zero-day flaw and protects users from potential attacks.

Owners of the Nokia 9 PureView have had a rough go with the in-display fingerprint sensor they've bought their phones — our Ryan Whitwam was not impressed with the fussing around and finger-jambing he had to do in order to achieve authentication. A software update last week was supposed to loosen up and get the sensor working as it should. But manufacturer HMD Global is now investigating a complaint saying that the phone is too loose, producing false positives from unknown fingers and even a packet of gum.









