latest
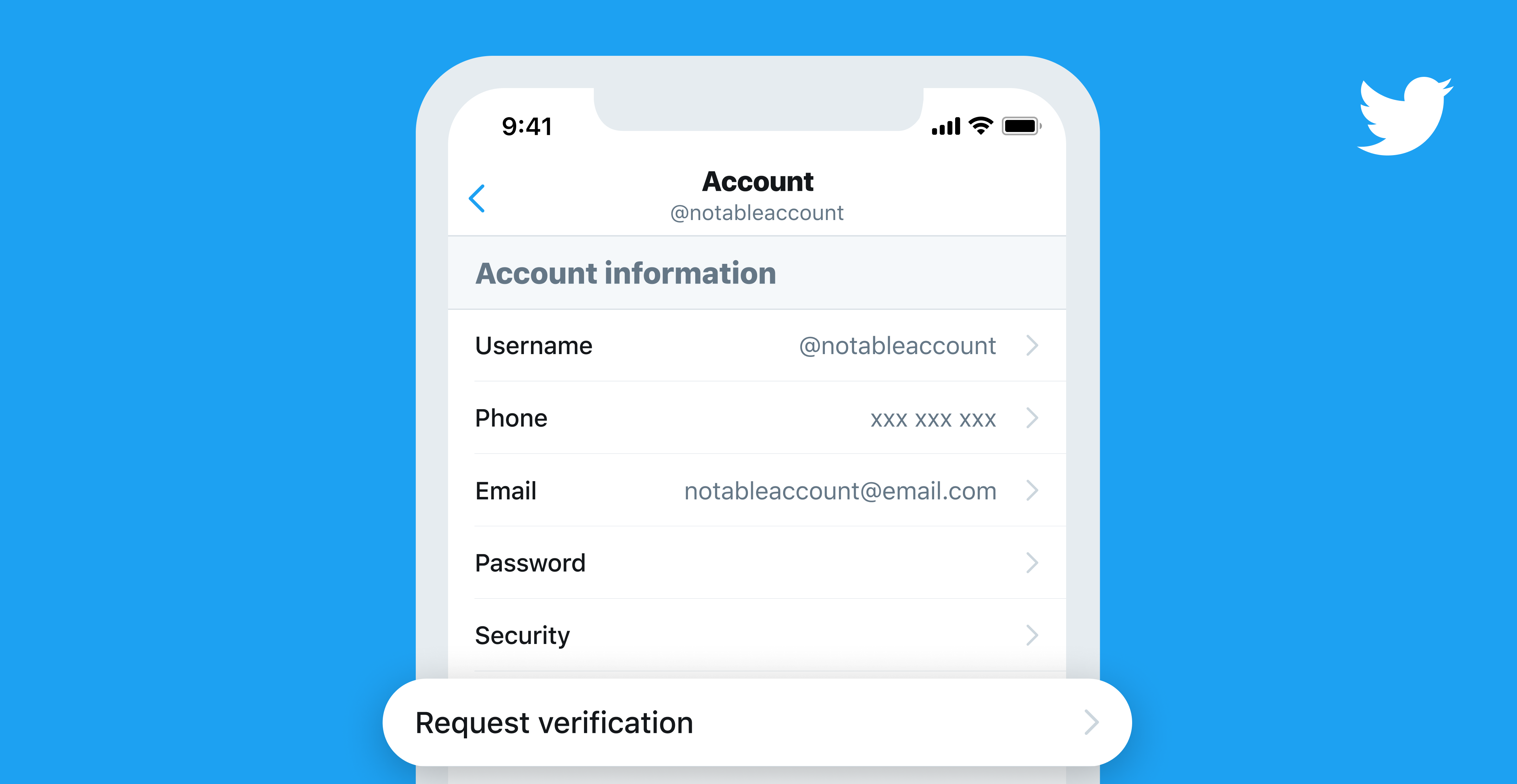
Your chance to apply for Twitter verification is finally arriving
The answer's 'no,' obviously, but at least let yourself pretend you've got a chance
Read update
After announcing an overhaul of the verification process late last year, Twitter is nearly ready to start accepting submissions. The company's spent the past few months gathering feedback from the public to make sure its new approach doesn't present any glaring issues, and this week announced that the option to apply for verification is finally starting to appear.

Google Autofill on Android can require biometric authentication now
Just like most other autofill providers
Read update
It's been a couple of years since the Autofill API was added to Android and you've been able to use Google or other password managers to fill in your credentials and log in to apps. However, while most third-party password apps require you to verify your identity before releasing your details to another app, Google's autofill just surrendered those details willy-nilly as long as your phone was unlocked. That's not so secure. A recent change to Play Services fixes that by letting you require an on-the-spot authentication before Google autofills the data fields.

Twitter has quite a troublesome history with verified accounts. For a long time, it's been unclear when an account qualifies to get the blue checkmark, and following controversy over verified white supremacists in 2017, the company essentially halted the program, promising to revamp it in the future. It looks like that time is about to come, as app sleuth Jane Manchun Wong spotted some code on the Twitter website pointing to a "Request verification" option in Settings.

Following last week's report that thousands of verified YouTube accounts, including Android Police, could lose their verification checkmark badges, YouTube executives have decided to backpedal on their initial announcement.

YouTube has always been one of Google's less conventional properties, but the sudden leap from version 6.0 to 10.0 gave everybody a surprise. Even stranger is that with such a substantial jump in versions, there are virtually zero meaningful changes to the user-facing features. While there's relatively little for us to enjoy right now, a full teardown reveals that there are at least a few additions that might be worthy of a major version bump.

You hear a lot of reports about malware and other undesirable third-party apps these days, especially from security researchers (and people who want to sell you something to make you feel safe). It's undeniable that malicious apps are a problem on an open system, but new data from Google indicates that the amount of actual harm being done might be negligible. QZ.com reports on a presentation from Google's Android Security Chief Adrian Ludwig at the Virus Conference in Berlin. He estimates that .001% of Android apps are able to get past Google's defenses.

Remember when Google's app verification and malware scanning service debuted with Android 4.2? No? Well, that's probably because statistically speaking, you're likely to be one of the 95% of Android users rocking 4.1 or earlier. To help address this, it looks like Google has moved the Verify Apps system to Google Play Services, which at this point should be installed on all Google Play Store-equipped Android devices running Gingerbread or higher. The change was spotted by JR Raphael at ComputerWorld.


[Update: 8/24/10 @ 7:45 PM EST by Aaron] Tim Bray responded to Justin's article, but seems to have misunderstood the goal. Thus, Justin has written a follow-up article here.







