latest
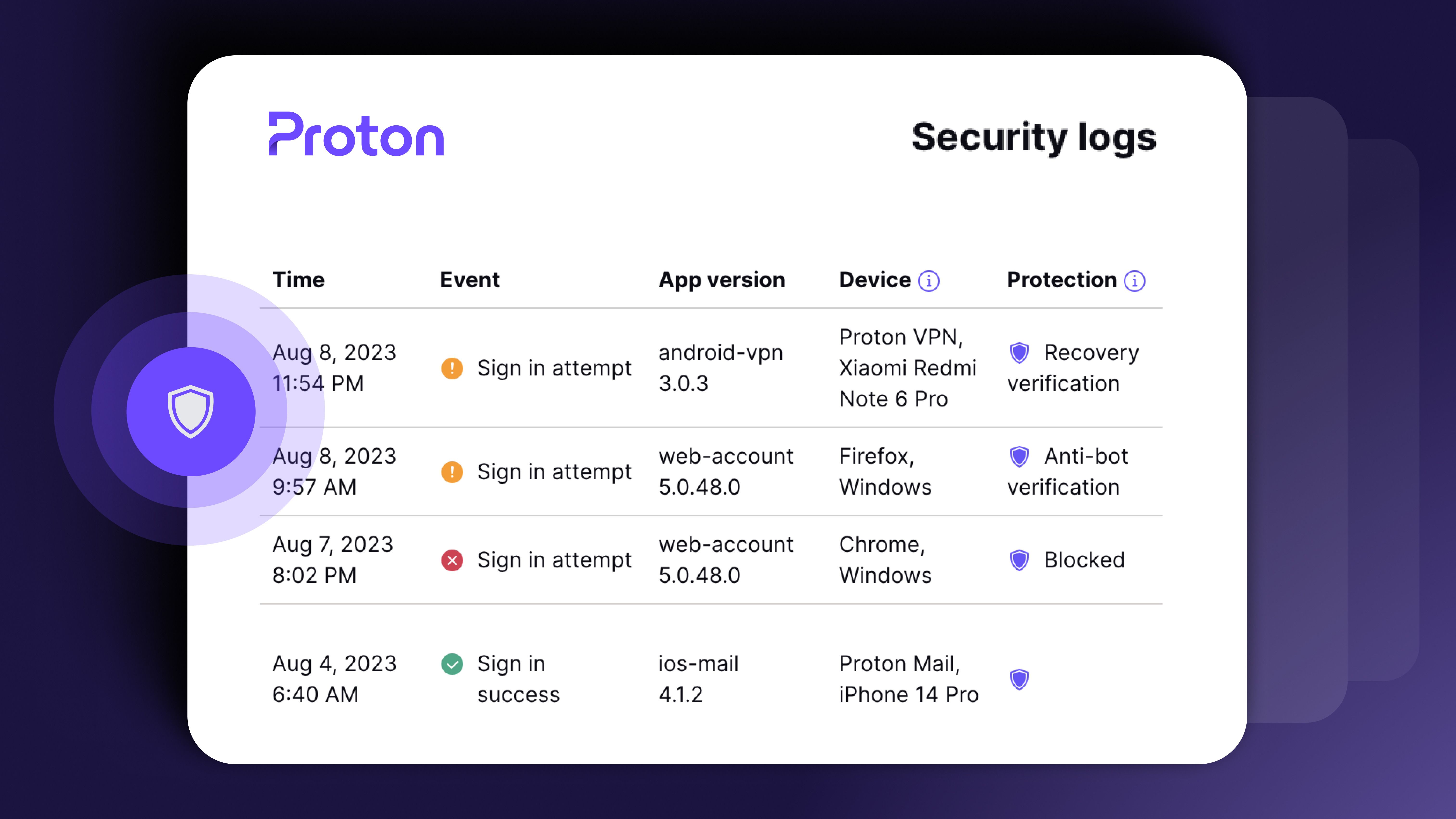
Latest Proton Pass enhancement could give it an edge over the competition
Sentinel adds an impressive layer of security, and subscribers no longer need to pay extra
If you’ve ever had your email hacked, you know how frustrating and time-consuming it can be to recover your account. Safeguarding your inbox is a step you can take to prevent a security breach from happening altogether. Now, Proton Pass wants to make it easier for its Plus subscribers to take this step — its high-security Sentinel program is now accessible to members in this tier.

Chinese hackers are using VLC media player to launch malware attacks
The likely state-sponsored hacks began in 2021
VLC is a super-popular media player for good reason: It's free, open source, and available on just about every platform imaginable. Plus, it can handle basically any audio or video file you throw at it. VLC is also light on resources, meaning it won't slow down your Windows computer — unless, perhaps, it's hiding malicious software. A new report indicates that's entirely possible, due to the efforts of a notorious Chinese hacking gang.

Lapsus$ may still be hacking even after alleged members were arrested in the UK
Someone is still posting links to stolen data on the group's Telegram channel
Just because police in the United Kingdom have arrested some alleged members of the hacker group Lapsus$ doesn't mean that the group is finished terrorizing big tech. It looks like some bad actors are active and causing trouble, using various methods to steal information and disrupt businesses. Arrests and charges are a positive step, but Lapsus$ is still hacking away.

Hackers sure have been busy the last couple weeks, warns Google's Threat Analysis Group
Get the hack out of here
Hackers and hacking groups have been busy finding new ways to use the war in Ukraine as a lure in their phishing and malware campaigns. Organizations and possibly individuals based in Russia, China, North Korea, and Iran are just some of the government-backed — and, occasionally, independent — bad actors who have used various war-related themes to get people to click on malicious links. While many of these attacks aren't always sophisticated, they can be hard to detect and block, so tech giants like Google have to have their own cybersecurity army at work 24/7.

Hackers funded by state money have been fighting battles online for years. With the ongoing Russian invasion of Ukraine, the cyber warfare front went from a simmer to a boil. While the combatants on the ground and in the air at the moment are primarily from two countries, reports from Google's Threat Analysis Group (TAG) indicate there are more players involved in cyberspace, including hackers working for China's military.

CISA issues warning that Russian hackers are bypassing two-factor authentication
2FA is great, but not perfect
Two-factor authentication (2FA) can be an important component of the steps you take to keep your accounts and data secure, but it's not without its flaws. As if the existing threats weren't concerning enough, now we're learning about how Russian state-sponsored hackers are undermining authentication in supposedly secure systems and disguising their access as that of legit account holders.

Linux Dirty Pipe kernel bug exposes Android to potential malware vector
Get ready to clean those dirty pipes
If Android were a car engine, and you popped the hood and poked around a bit, you'd find the label "Linux" etched on the engine block. The open-source operating system provides the starting point that Android's built on top of, but sharing code also means sharing vulnerabilities. Now a newly discovered Linux kernel bug is raising concerns for the security of Android devices, as it leaves a door open for malware intrusion.

Just after Russia invaded Ukraine on February 24, US-based chipmaker Nvidia was hacked. It wasn't a minor incident — cybercriminals managed to take down vital services including email and developer tools. While the timing there fueled suspicion that the attack could be connected to the invasion somehow — after all, Nvidia chips are in devices everywhere, making it a valuable target — it's since become apparent that we're instead looking at a crypto-motivated shakedown attempt.
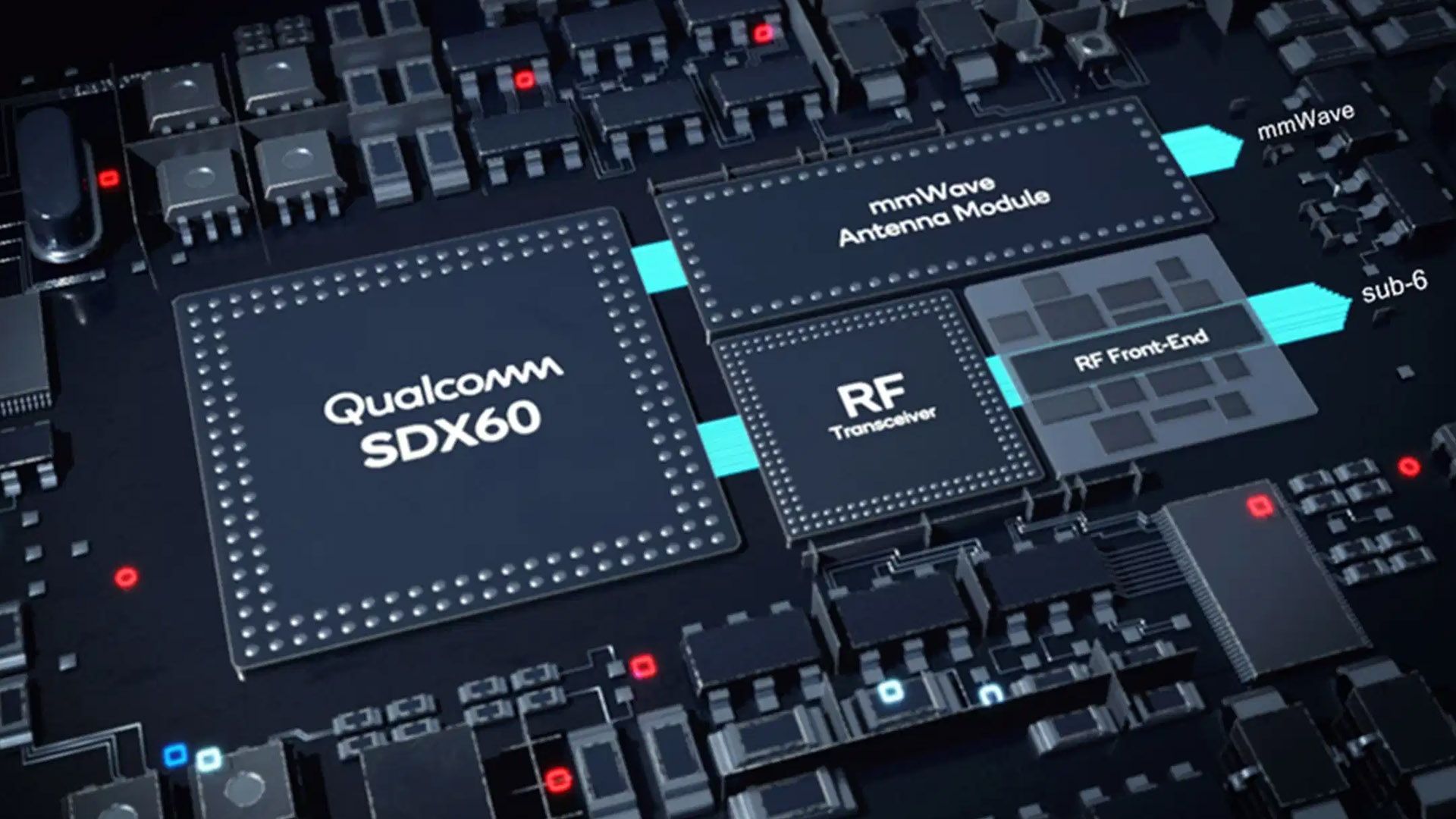
Samsung phones already protected against modem vulnerability that lets hackers listen to your calls
The Qualcomm issue affects an estimated 40% of Android phones
Read update
Google and other Android manufacturers try to keep on top of the hardware and software security, at varying degrees of intensity. But a vulnerability in widely-used Qualcomm SoCs disclosed by Check Point Research today was particularly alarming. It could theoretically allow a malicious app to patch the software for Qualcomm's MSM modem chips, giving it access to call and text history or even the ability to record conversations. Thankfully, most Samsung phones have already received a patch fixing the problem, and the rest is in for an update next month.

Aptoide database breach exposes 20 million user accounts, possibly more to come
At least there aren't any payment details to worry about
Website hacks are nothing new, and it's all but certain that everybody has had at least at least a couple login credentials and other details exposed at some point. Unfortunately, another incident has occurred, this time with the Aptoide app store. Minimal personal information and zero payment details were exposed, but login credentials are exposed.

Pokémon Go update blocks players if custom recoveries are detected
The game won't run if it finds a 'TWRP' or 'Fox' folder on your phone
Niantic Labs' cat-and-mouse game with Pokémon Go cheaters has led to many instances of innocent players being locked out of the game. Only a few months ago, owners of some Xiaomi devices had their accounts suspended for no fault of their own, and now Niantic is seemingly cracking down on players with custom recoveries installed.

The first day of the Pwn2Own hacking contest held in Tokyo has concluded, and a dual-member team of white-hat hackers by the name of Fluoroacetate cleaned up the house. After successfully hacking past numerous devices from multiple manufacturers, such as Samsung and Xiaomi, the team collected a bounty of $145,000 and secured a commanding lead in the contest after accruing 15 Master of Pwn points.Pwn2Own is an annual computer hacking contest that started in 2007, and its name is derived from the fact that contestants must "pwn" or hack the device in order to "own" or win it. The purpose of the contest is to demonstrate the vulnerability of devices and software in widespread use. All the bugs and exploits used during the competition are handed over to the event organizers, who in turn forward them to the respective vendors. For each successful takeover of a device, the contestant wins prize money and points that count toward an overall ranking. The winner earns the title of Master of Pwn.

Identity theft via hacking or social engineering is a common problem these days, and the results can quickly spiral out of control, locking you out of the accounts you depend on permanently, as in the case of today's horror story. A contributor over at ZDNet recently suffered what can only be called a total security meltdown in the space of a week when a hacker gained access to his Google account via a SIM-swap attack.

It's open season on email hackers, tracking cookies and Facebook shadow profiling as our favorite open-source software makers at Mozilla have released a series of updates for its Firefox web browser, Firefox Monitor service, and its Facebook Container, as well as rounding out a series of mobile password managers with a new extension called Firefox Lockwise.

Checking your credit card statement after wondering why your balance is so high and finding transactions that you don't recognize is among life's most uncomfortable moments. Many of us have been there, and even though you know there's a good chance you'll get the money back, that feeling of violation is hard to shake. Unfortunately, some recent OnePlus customers are going through exactly that at this moment in time.

Sometimes inaction can be just as dangerous as making a wrong move. That seems to be the case for Samsung, as it appears simply letting a domain expire could have left millions of its customers vulnerable to hackers. Luckily, a security researcher named João Gouveia noticed the potential problem and snapped up the domain before anyone with more nefarious intentions was able to grab it.

The ability to unlock a device with your face is nothing new - Android had it back in 4.0 Ice Cream Sandwich. But recently, we've seen more complex eye unlocking technology crop up on consumer electronics, such as Windows Hello. The Galaxy Note7 and S8 included something similar, called the Iris Scanner.
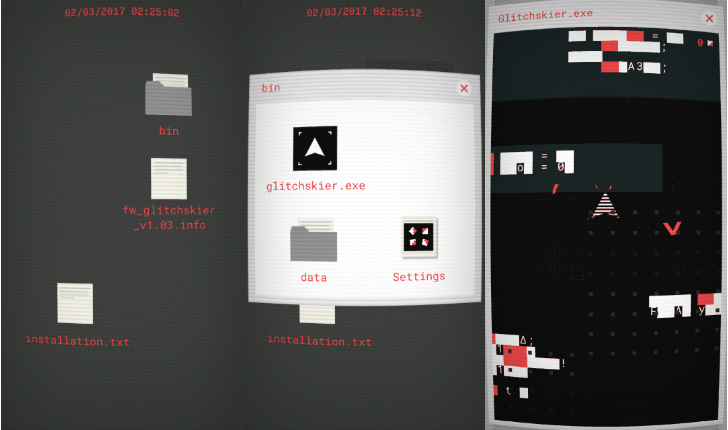
Heard of Mr. Robot, the popular USA show that features developers, hacking, giant, evil corporations, and computers? If so, listen up: Glitchskier is a game where the player hacks the computer to progress, defeating enemies, boss fights, and the system itself.

One of the more interesting things to emerge from the digital revolution is hacking competitions and prizes, wherein benevolent "white hat" hackers are invited to try and defeat hardware and software in a closed environment. The latest mobile-only edition of the Pwn2Own competition was sponsored by software security company Trend Micro, offering cash prizes to anyone who could get user info, install rogue apps, or completely unlock some of the biggest mainstream phones out there: the Nexus 6P, the Galaxy S6, and the iPhone 6s.










