latest

Wi-Fi vulnerability affecting WPA2 encryption makes older Android phones insecure
Most currently supported devices have likely already been updated
These days, most people connect to the internet via Wi-Fi. We've been taught that on unprotected, open hotspots, you can easily be followed around the web, but generally, we would assume that password-protected networks are relatively safe from outside attacks. As it turns out, a vulnerability in the widely used Wi-Fi protected access 2 (WPA2) protocol lets hackers view unencrypted connections on these networks, even if they don't know the password. Patches are already rolling out to current routers and client devices, leaving only older, unsupported hardware indefinitely affected.

Yesterday, security researchers at AdaptiveMobile Security revealed the existence of a new exploit they call "Simjacker," which they say allows for remote surveillance from targeted phones (among other potential actions) using nothing more than a malicious SMS. They even claim that the exploit has been actively used over the last two years by "a highly sophisticated threat actor in multiple countries." It all sounds like a pretty big deal, and unfortunately for concerned consumers, the researchers leave plenty of unanswered questions.

Another day, another major security hole is found in a widely used piece of software. This time around, a flaw in Chrome's implementation of the FileReader API allowed sites to break out of their sandbox and execute native code. To make matters worse, Google said the exploit was being actively used before the company fixed it.

Amazon released the Fire TV Cube earlier this year, as a 4K-capable streaming device with far-field microphones (for responding to Alexa responses) and an IR transmitter (for turning devices on/off). Exploitee.rs has now released a root method for the Fire TV Cube and the 2017 Fire TV Stick, which relies on sending commands through the HDMI port and bypassing code verification.

Over the past few days, we've covered an issue with the Harmony Hub not being able to control Sonos speakers' volume properly, which was followed by a fix with firmware 4.15.100. As it turns out, the issue occurred because Logitech may have rushed to release firmware version 4.15.96 for the hub to patch a vulnerability discovered by FireEye.
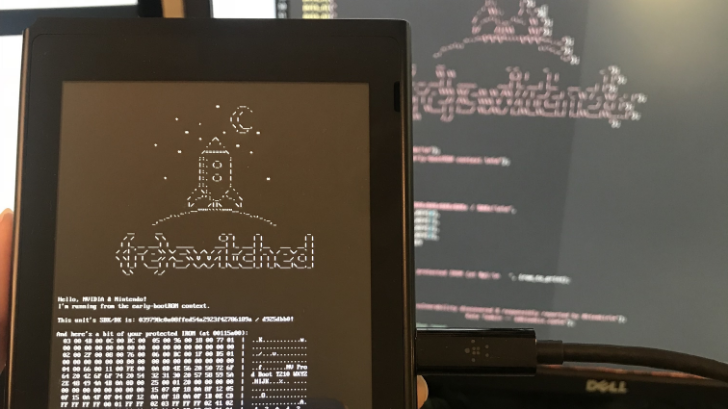
The Tegra X1 is one of Nvidia's latest mobile processors, powering devices like the Nintendo Switch, Google Pixel C, and Nvidia Shield. It's not uncommon that vulnerabilities are discovered in SoCs, and that has just happened for the Tegra X1. Katherine Temkin and the ReSwitched hacking team have just released details about a security flaw, nicknamed 'Fusée Gelée,' that allows unauthenticated arbitrary code execution on devices using the Tegra chip.

Read update
- NowSecure, a mobile security company that helped the developer find the password, has published a more detailed writeup about the backdoor. The post reveals that the poorly-hidden password was in fact "angela," possibly a "Mr. Robot" reference to character Angela Moss.
Just a month ago, OnePlus was caught collecting personally identifiable data from phone owners through incredibly detailed analytics. While the company eventually reversed course on the data collection, another discovery has been made in the software of OnePlus phones. One developer found an application intended for factory testing, and through some investigation and reverse-engineering, was able to obtain root access using it.

The Samsung Smartcam is a great example of why consumers should be wary of 'Internet of Things' devices. Multiple exploits for the camera have been found since the Smartcam initially went on sale, previously allowing for remote command execution and changing the admin password without knowing the original one. Now another exploit has been discovered for the Smartcam, this time allowing commands to be executed as the root user.

Android developer extraordinaire Chainfire has worked his magic again, releasing a new beta of SuperSU with support for the Galaxy Note7. There are a few caveats though, mostly due to new Samsung security measures inherent in the kernel, stopping Chainfire from using his usual exploits and instead having to apply workarounds.

Ask anybody that spends time in the security circles and they'll tell you that every large software project is bound to have a few long-standing vulnerabilities in the code. Fortunately, there are usually a few people who are paid to close up those holes so you, the customer, don't find yourself the victim of nefarious evildoers someday. Like so many before it, the latest update to Android came with a boatload of changes, at least one of which fixes a potentially dangerous vulnerability that can be used for numerous attacks, including a way to acquire root.

SuperSU Security Advisory: Update To Version 1.69 (Available Now) To Avoid Potential Exploits
SuperSU Security Advisory: Update To Version 1.69 (Available Now) To Avoid Potential Exploits
If you're a root user, listen up. Chainfire updated SuperSU to v1.69 as of last night, which fixes two exploits that could allow an attacker to leverage root privileges without first prompting the user. Probably nothing to get overly anxious about, but it's definitely a good idea to make sure you're running the latest. Details of these exploits will be released next Monday, so you'll want to grab the update before then.

The second annual Mobile Pwn2Own competition, run by HP TippingPoint's Zero Day Initiative, is fast approaching. This year's event will take place at the PacSec Applied Security Conference in Tokyo from November 13-14, and over $300,000 in cash and prizes is up for grabs. The Pwn2Own contest challenges security researchers to find and exploit vulnerabilities on mobile devices and rewards them by giving them the device they were able to compromise. In short, a contestant must "pwn" a device in order to own it. This year's event is sponsored by Google's Android Security Team and BlackBerry.

Since Dan Rosenberg declared his intentions to stop publishing exploits for Motorola devices, fans of the OEM have been wondering if there will be much of a future within the modding community. While the distant future is still very foggy, Justin Case has come to the rescue with his own rooting method for Motorola's latest salvo of devices. His simple-to-use app roots the Moto X, Ultra, Mini, and Maxx.

When it comes right down to it, few things are much scarier than finding out somebody can track your movements, read your call log and text messages, and even record audio and take pictures of whatever the phone can get, all without your knowledge. Here's the thing - as careful, security-conscious people, many of us already install software like that for our own purposes, usually to recover a phone in the event it should fall into the hands of thieves. Like a weapon intended for protection, sometimes our best defenses can be turned against us.
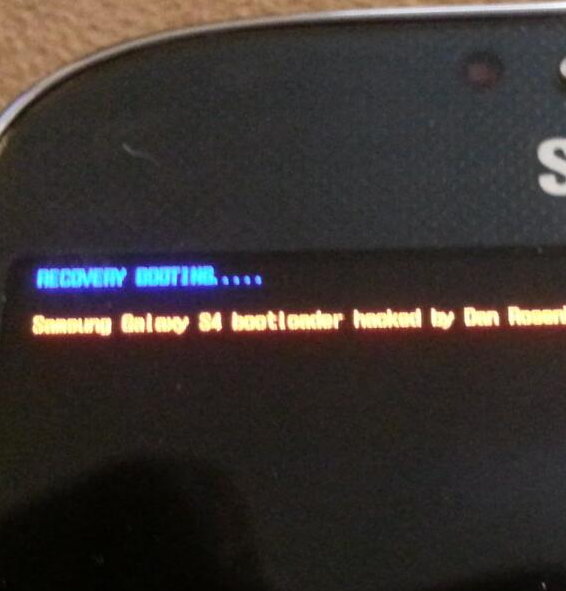
[Updated: Q&A] Dan Rosenberg Has Unlocked AT&T Galaxy S4's Bootloader, But We Won't Get To See How For A While - Here Is Why
It was only yesterday that Cyanogen definitively confirmed AT&T's treacherous move to lock down the Galaxy S4's bootloader, but there is light at the
It was only yesterday that Cyanogen definitively confirmed AT&T's treacherous move to lock down the Galaxy S4's bootloader, but there is light at the end of that tunnel. No thanks to AT&T but to security researcher extraordinaire and a person I admire Dan Rosenberg, a.k.a. the magician, a.k.a. the root whisperer.

When it comes to root and mod action on Motorola devices from the last couple of years, all eyes turn to brilliant Android hacker Dan Rosenberg. Since the Droid 3 was released two years ago, Rosenberg has successfully found root exploits for every Motorola device, including the D3, Bionic, RAZR, Droid 4, Xoom 2, Atrix HD, RAZR HD, and RAZR M. Add to that the fact he just released a tool that unlocks the bootloaders on the most modern Moto phones (RAZR HD, M, and Atrix HD), and it's not hard to see why he's such an important part of the Motorola modding community. Heck, without him, there probably wouldn't even be a Moto modding community.

There's some disturbing news today on the Android security front: an vulnerability has been discovered for Samsung's Exynos 4-powered devices. While the related exploit is useful for the mod scene in that it can be harnessed to gain superuser permissions and root pretty much any device running on an Exynos 4 chip, it's also got some rather disturbing implications. According to an XDA member with the handle "alephzain", who developed the exploit, using this security hole can also grant an app access to all physical memory on a given device - basically, anything stored in RAM is fair game. The virtual directory for memory within the kernel, dev/exynos-mem, is wide open, apparently for access to various camera-related functions.

Update 2: This exploit probably won't work on most Galaxy S III's as long as they have the most recent OTA update, as we demonstrate on video here.












