You probably don’t wake up in the morning worried that your phone is going to outright betray you. Malware and security snafus are one thing, but updates keep that boogeyman away. And even though we read about bad guys caught by Stingrays and dirtboxes (false cell towers), that’s just something authorities use to keep us safe — right? Whatever your opinion on that can of worms that I probably shouldn’t have mentioned, it’s also getting easier for criminals to build them now, too. A demo cell site at Qualcomm’s recent event even caught an analyst’s phone. But companies like Qualcomm have been working on ways to mitigate that.
Full disclosure: Qualcomm flew me and dozens of other journalists, analysts, and content creators to its Snapdragon Summit media event in Hawaii. It’s hot out, we’re all masked up, and I’m pretty sweaty.
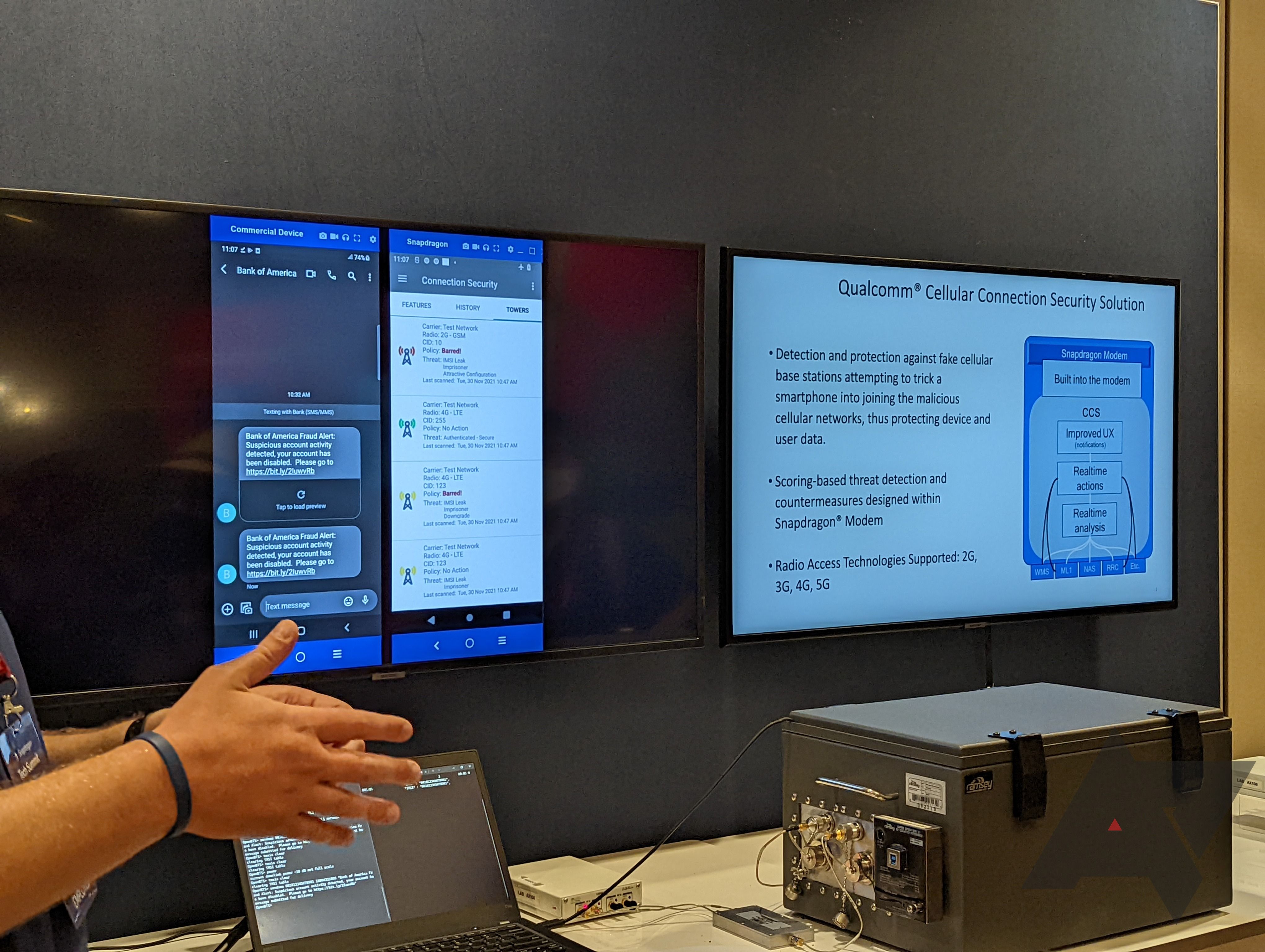
At the Summit, Qualcomm had a demo set up to show how its phones can detect these Stingray cell sites and their tricks. You might not be aware of it, but these types of software-defined cell towers are getting cheaper and easier to build — Qualcomm had one sitting in a box on a table, made with easily available hardware and almost fully open-source software, making it pretty simple to put together. It’s not just something that state-level actors or the police can afford to do anymore. And they aren’t just used for tracking locations or intercepting communications. Like everything these days, they can be used for spam, too.
I can’t say it’s an issue I’ve personally run into just yet, but Qualcomm showed a demonstration of an SMS message sent by a cell site simulator posing as a bank reporting fraudulent transactions. This is the same sort of spam message junk some of us get on a daily basis, but the fake cell site’s message is more convincing. You might not be aware of this, but SMS messages aren’t encrypted, and from its man-in-the-middle vantage, these fake towers can send messages that look legit, seemingly from the right phone numbers. Toss in a link to a malicious site, and what seems like a trustworthy message might be anything but.
There’s not a whole lot you can do to prevent that directly. SMS is an old, bad standard (hence why folks like me are so gung-ho about things like RCS messaging, which can allow for end-to-end encryption). But if you can’t stop the messages being delivered, you can at least stop devices from connecting to fake cell sites that send them.
See, the way these sites work is by making themselves more attractive to your phone. If you’re wandering around town, already connected to a legit cell tower, these fake ones need to do something special to stand out as a good choice for your phone to switch to. They do it with things like higher signal strength and by not offering a list of neighboring towers for easy hand-off, making devices likely to leave them (among other more technical configuration settings). Like a data-filled pitcher plant, it’s poised to snare phones in its trap and do everything it can not to let them go.
At the demo I saw today, the demonstration cell site even snagged Moor Insights & Strategy senior analyst Anshel Sag’s Galaxy S21 Ultra, handing it the nefarious example message we were shown on a demo phone. These things really do work!
Thankfully, those attractive attributes actually make it easier to detect the bad cell sites, and phones can see things like a lack of listed neighbors or too-high signal strength as concerning attributes, and Qualcomm’s modems can detect that. In fact, the logic for this runs fully inside the modem itself, separately from the OS or the rest of the chipset. The usual black box warnings apply: It’s probably more secure and probably can’t be affected by on-device malware, but you have less of an idea of what’s going on in there.
This isn’t an entirely new concept, and Qualcomm says its modems have had this technology for 2G, 3G, and 4G networks for some time (and, via the transitive property, 5G NSA, which relies on a 4G backbone to connect). But the new X65 modem, available in the Snapdragon 8 Gen 1, brings that detection to standalone 5G networks. And when it finds a potentially untrustworthy cell site, it either deprioritizes it (if it’s merely suspicious) or outright blocks the connection if it’s a real stinker.
But if you absolutely have to connect to one of these suspicious cell sites, Qualcomm also plans to roll out a whole set of APIs for developers as part of an SDK that can allow apps to make informed decisions on their own too. That could mean a banking app that won’t trust these suspicious connections to protect you from a man-in-the-middle attack or a messaging app that disregards or applies a warning label to SMSes that land when connected to Stingrayed towers. Unfortunately, I’m told this side of things is not ready quite yet, but the APIs are coming.
All of us ignore our digital security more than we probably should. It’s a subject that’s hard to make appealing or present as a big killer feature in the same way that we talk about, say, speed gains or camera improvements. Being safe isn’t a fun new toy. But this is one of those things that won’t need any effort on your part to make your life better, though developers will have a bit of work to do once those new APIs are available to detect these spoofed cell sites.