Read update
- scrcpy v1.18 and Android 12
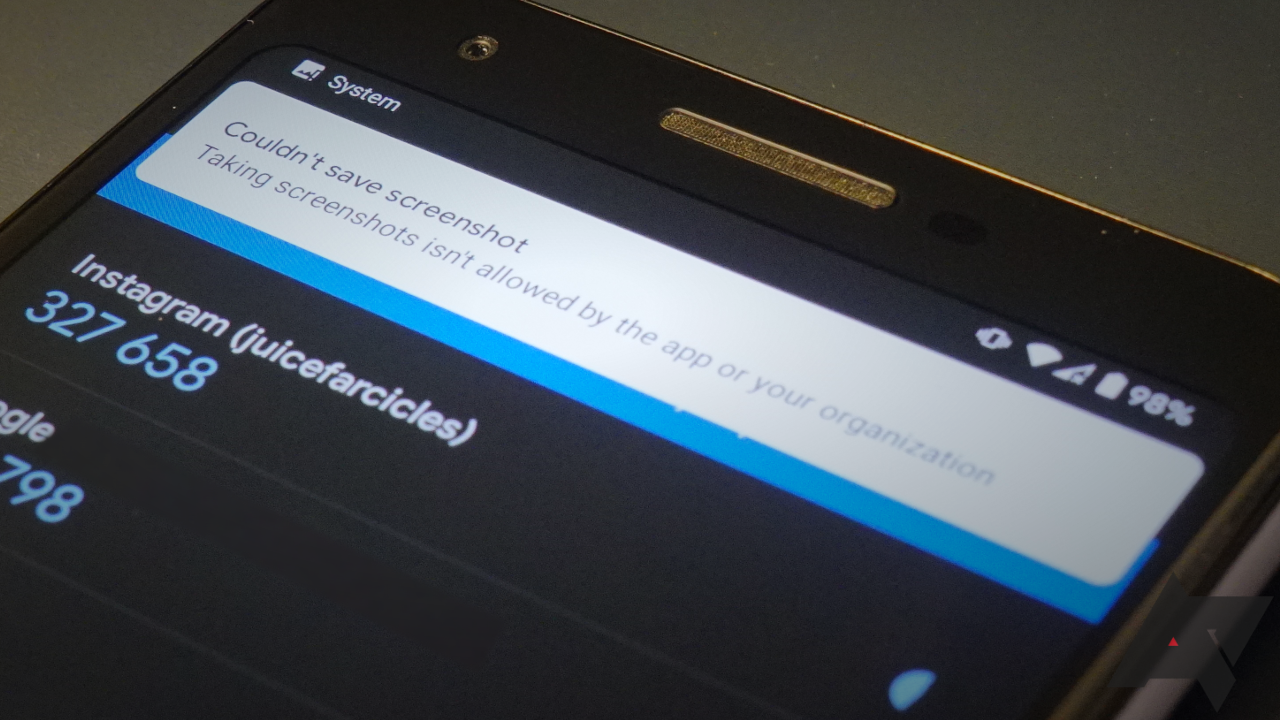
Android may be a wide-open world compared to iOS, but there are still some things you just can't do on Google's mobile platform. One of them is capturing screenshots within apps that prohibit the act — either because the screen contains sensitive information or content protected by digital rights management. Lucky, then, that we have a trick up our sleeve called rooting! Yes, even in 2020, it still has utility for the people who need it the most. So, if you'd like to grab a freezeframe to meme up or spoil a drama series or keep some backup passcodes where you can easily pull them out, we've got a way (or three) to do that.
There are at least a few ways to circumvent screenshot prohibitions in apps. Some that don't work include using a video capture app or using Google Assistant to make a snapshot — the output either gets blocked or distorted, as seen below in Amazon Prime Video.
We've updated our write-up again to include some solutions that were suggested by people in the comments below — thanks to them for those suggestions! One method requires connecting to your computer, the others will need root.
scrcpy (ADB tool)
This is scrcpy. Since writing this article, I have figured out that it's a portmanteau of "screen copy," but no matter how you pronounce it, this command prompt program lets you mirror, interact with, and record your Android device's screen. In other words, scrcpy has wider uses than just taking screenshots, but hey, better overkill than underkill, right? You can get the app for Linux, macOS, and Windows from this GitHub page.
Make sure your phone or tablet has USB debugging turned on. Once you've got scrcpy downloaded and exposed, pop open a console or command prompt from the file's location and execute:
scrcpy -r nameyourfile.mp4
It'll record a video of your device's screen in its full resolution. For some installations, you can end the record session by hitting Ctrl+C. Others will need to disconnect their device. You can configure a raft of aspects such as orientation, framerate, and size with commands that can be found here.
Of course, you could just not bother and use your computer-based capture tool of choice to take some shots. In this case, the output quality is highly dependent on your monitor, save for if you're forcing a higher resolution, but you can definitely use scrcpy in this manner. If you're just picking up a bunch of passwords or login codes — Google Authenticator v5.10 isn't the best example to use, but you're able to use the tool on Chrome Incognito tabs unlike most on-device screen recorders — you're pretty much fine here.
Some purposes, though, are a waste of scrcpy. If you're on a computer anyways and have a Netflix or Amazon Prime account, you're better off with a screencap your favorite show from a browser instead.
UPDATE: 2021/12/27 09:18 EST BY JULES WANG
scrcpy v1.18 and Android 12
It looks like Android 12 is the end of the line for scrcpy. Earlier this year, news came out that the new OS version has essnetially blocked the avenue in which the program allows users to screenshot content from apps that block the action.
In short, the OS requires a privileged or 'secure' display to show secure content and scrcpy, through adb, was able to create a secure display instance on your computer. That's no longer possible on Android 12.
If you want to expend not too much effort on your screenshots, consider using scrcpy with an older device.
But what if you happen to be watching something and you've only got your phone with you? Well, the good news is that it's possible to skip around the screenshot security fence. The (slightly) bad news is that you'll have to do some homework in the first place.
SmaliPatcher (Root, Magisk)
Unlike scrcpy, root methods seek to disable apps from setting FLAG_SECURE, which blocks users from screenshotting or recording content in the first place.
This is not a comprehensive tutorial on how to root your device because that's not what you came to this particular article for (hopefully). The initial process is different from device to device and there are other things we'd want to explain in detail that we can't do here for brevity. There are probably plenty of articles you could search for to help you out, no matter your expertise or where along in the process you are in.
Here are some convenient links to basic resources if you happen to need them:
From this point on, though, we're going to assume you have a rooted device.
The good thing about this method for attaining screenshots where you usually can't is that it ultimately works as a Magisk module. But while you do need to "create" the module yourself, you can do it in 5 to 10 minutes with a simple tool called the Smali Patcher courtesy of fOmey, a developer and XDA forums regular — you can check out their full write-up here or get straight to downloading the tool either here or with this Google Drive mirror link.
Now, we'll take it step by step:
- Make sure your Android device has USB debugging enabled.
-
Fire up your ADB tool on your computer and connect your phone. Make sure your phone's recognized by executing:
adb devices
- Download and extract SmaliPatcher-0.0.6.7-fOmey@XDA.zip, then run SmaliPatcher.exe
SmaliPatcher requires your computer to have at least 3GB of RAM, .NET Framework 4.7.1 or later, Java, and an Android 6.0+ device.
- There are plenty of great patches you can apply here, but the one that we want here is Secure flag. Select that checkbox and hit the ADB PATCH button below.
- The tool will then generate a patch that will eventually appear in the same folder as SmaliPatcher.exe named SmaliPatcherModule-0.0.6.7-fOmey@XDA.zip
- From there, you can sideload it onto your phone, open Magisk, hit Modules in the side menu, tap the + icon, and select that zip file. Then, reboot the device.
- Or you can boot into your recovery and load the zip file through an ADB sideload command.
And we've landed! Despite fOmey's disclaimer that some of the tool's patches may not work with Android 10 devices, we were able to make it happen with our Pocophone F1.
Kim's Convenience / CBC, Netflix
Unfortunately, a number of apps won't fall to this patch — Amazon Prime Video, banking apps, and others still shot-block you — so your mileage may vary here. But if you need to grab a still on your phone by any means necessary, this will be a good bet.
Xposed (Root... and Magisk for some users)
The alternate root route to go is to get the Xposed Framework working on your device — there's a simple module that just disables the system's secure flag.
If you're still using a device on Android 4.0.3 to 4.4 (most versions of Ice Cream Sandwich, Jelly Bean, or KitKat), follow the instructions from the official Xposed repository. For users on Android Lollipop, Marshmallow, or Nougat, you'll get your directions from this XDA forums page.
If you've already got Magisk on your Android Pie or 10 machine, you just have to obtain a module of a module (don't worry, it's actually not that hard). You'll need to install the Riru Core framework, the Riru EdXposed module, and then the EdXposed Installer .apk that will install the ultimate module in question. The above hyperlinks bring you to their respective GitHub pages — you can find the first two in Magisk's downloads section or grab the Core and the EdXposed module from GitHub and induce via recovery if you'd like.
Once you finally have the Framework in place on your particular device, download and install the DisableFlagSecure .apk from the Xposed repo. Then, go to your Xposed or EdXposed installer app, check the modules list and toggle DisableFlagSecure on. Reboot your device and thar she blows!
I won't bore you with more Authenticator and Netflix screenshots because yes, they do work.
I will share, though, just this blank grab from Amazon Prime Video — unlike the Smali method, you can take a screenshot on the app, but the content will be blanked out. All the difference in the world, I suppose.
However you do it, we hope you're able to get all the screenshots you need.