Every once in a while, a major security vulnerability is discovered in devices you use in your daily life that could put your privacy at risk. Recently, Google's Project Zero team revealed multiple remote code execution vulnerabilities in Exynos modems that could allow hackers to compromise some of the best Android phones like the Google Pixel 6 and Pixel 7 without any user interaction. Worse, they only needed to know the victim's phone number to achieve this. So, how can you keep yourself safe if you own an Android phone, watch, or even a car that uses an affected Exynos modem?
How bad is the Samsung Exynos modem vulnerability?
Very bad. In total, Google's Project Zero found 18 zero-day vulnerabilities in Samsung's Exynos modems. Out of these, four are critical issues as they allow for remote code execution without any user interaction. This allows a hacker to remotely compromise your phone at the modem level only by knowing your phone number.
Below are the CVE-IDs (Common Vulnerabilities and Exposures) of the four exploits:
- CVE-2023-24033
- CVE-2023-26496
- CVE-2023-26497
- CVE-2023-26498
It is unclear whether hackers have used these exploits in the wild.
Whatever the case, Project Zero's head Tim Willis believes a skilled hacker can take advantage of the exploit in no time to compromise the victim's phone. And because of the severity involved and a "very rare combination of level of access these vulnerabilities provide and the speed with which we believe a reliable operational exploit" can be crafted, the Project Zero team has decided to disclose the four exploits at a later date once they are fully patched.
As for the remaining 14 vulnerabilities, they are not as severe since they require the hacker to access the device or involve a rogue mobile network operator.
Which devices and Samsung modems are affected by the vulnerability?
As per Samsung Semiconductor's product security page, the affected chipsets include the Exynos Modem 5123 and 5300, as well as the Exynos 980, 1080, 1280, and 2200 processors.
The following devices are affected by the vulnerabilities in Samsung modems:
- Google Pixel 6 series, including the Pixel 6a
- Google Pixel 7 series
- Vivo S6, S15, S16, X30, X60, X70 series
- Samsung Galaxy S22 series
- Samsung Galaxy A04, A12, A13, A21s, A32s, A33, A53, A71, M12, M13, and M33 series
- Vehicles with Exynos Auto T5123 chipset
Initially, it was believed Samsung's wearable Exynos W920 chipset found inside the Galaxy Watch 4 and Watch 5 series was also vulnerable. However, that was incorrect, with Samsung updating its security advisory since the original announcement to remove any mentions of the chip.
How to secure your Google Pixel 6 or Pixel 7 from the scary Exynos modem vulnerability?
Google has patched all four critical vulnerabilities on its Pixel phones with the March 2023 security patch. You can go through the company's latest Android security bulletin to confirm this. Initially, the Project Zero team believed that Google had only patched one of the four vulnerabilities with this update, but that's not the case.
So, if you own any of Google's 2021 or 2022 Pixel phones, your best bet is to install the latest security patch to keep yourself safe from this scary vulnerability. As a bonus, the March Feature Drop also brings several new features to the phones.
While Google published this month's security patch details on March 13, the OTA update only went live for Pixel 6 users a week later, on March 20. There's always the option of manually sideloading the update if it still has not shown up for your phone.
Alternatively, you can disable Wi-Fi Calling on your Pixel until the March 2023 update appears for download. This can be done from Settings -> Network & internet -> SIMs -> Wi-Fi calling and turning off the toggle for Turn on Wi-Fi calling.
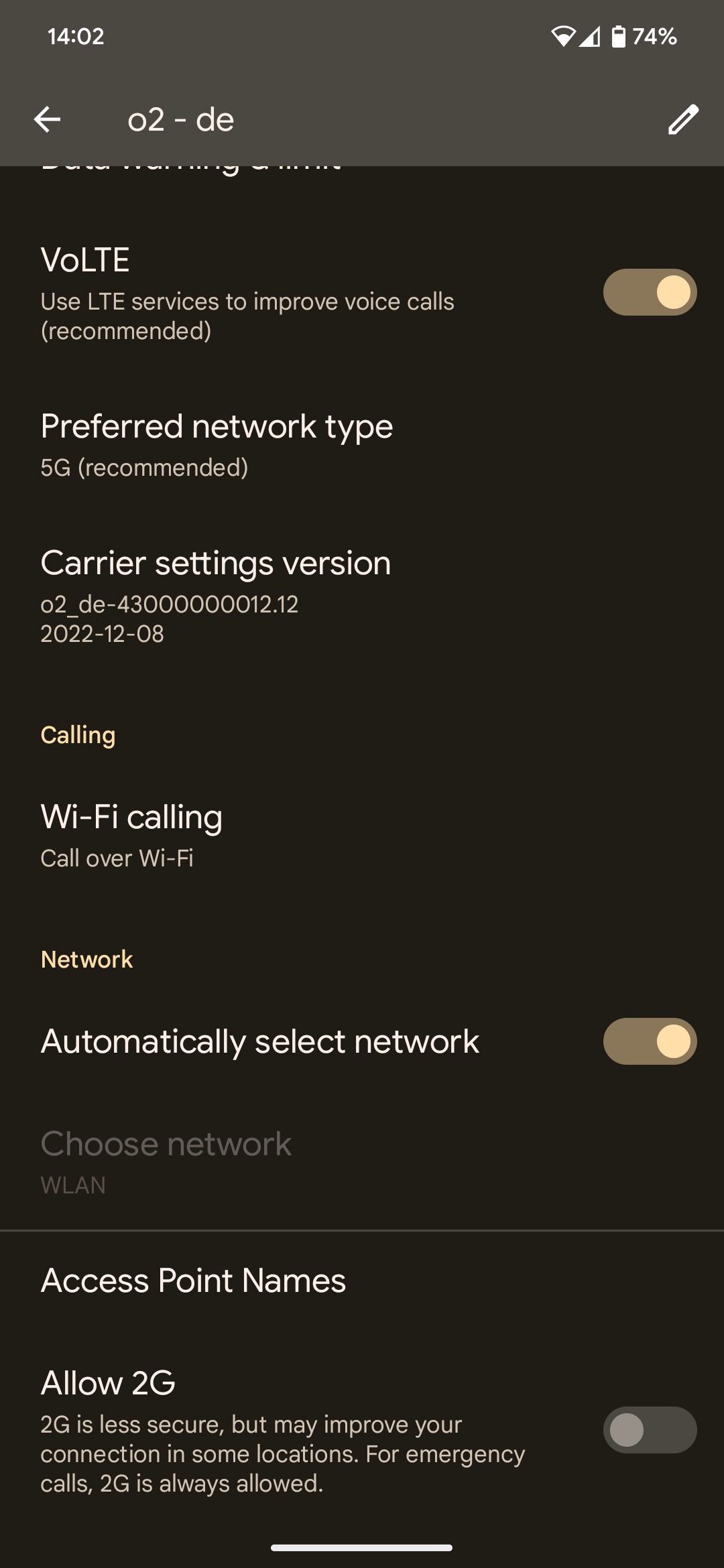
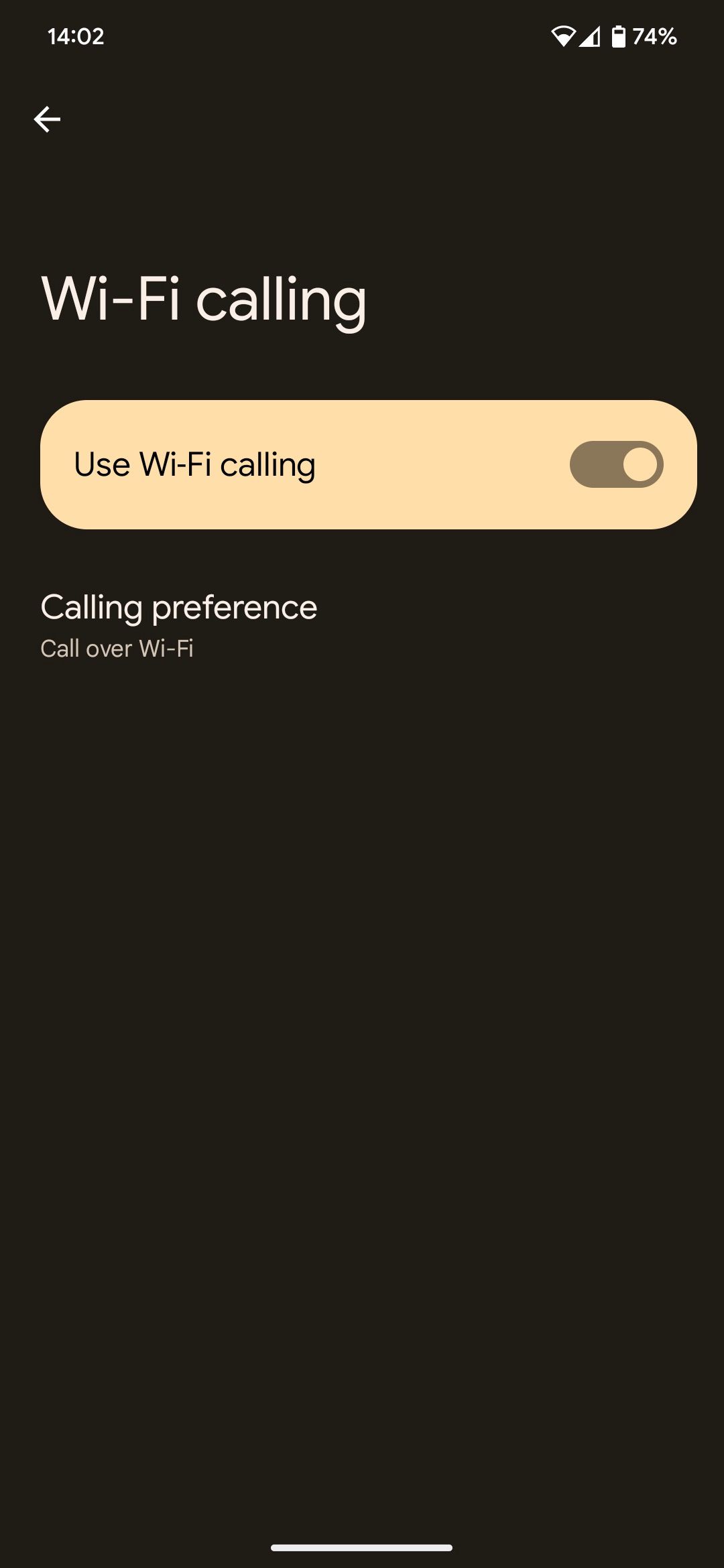
The catch is that there's no way to disable VoLTE on Pixel phones since this is a carrier-controlled toggle. Depending on your network operator, the option may appear under the Network and Internet menu, though your mileage may vary.
Many carriers do not support voice calling without VoLTE. So disabling VoLTE might affect voice calling on your phone.
While you should be fine until the March 2023 security update lands on your phone, you can disable SIM connectivity entirely on your Pixel 6 or Pixel 7 if the vulnerability bothers you too much.
How to secure your Samsung phone from the scary Exynos modem vulnerability?
Surprisingly, Samsung says in its statement to Android Police that none of the six identified vulnerabilities are "severe." Out of them, the company has already patched five exploits with its March 2023 firmware. The Korean giant will patch the remaining exploit with the April 2023 security update.
Below is Samsung's statement in full:
Samsung takes the safety of our customers very seriously. After determining 6 vulnerabilities may potentially impact select Galaxy devices, of which none were 'severe', Samsung released security patches for 5 of these in March. Another security patch will be released in April to address the remaining vulnerability. As always, we recommend that all users keep their devices updated with the latest software to ensure the highest level of protection possible.
Samsung was the first company to roll out the March 2023 security patch for its phones. Since the beginning of the month, the company has expanded its rollout to include almost all its popular flagship and mid-range devices launched in recent years. So you can safeguard your phone against this Exynos modem vulnerability by simply installing the latest firmware on it.
However, some low-end Galaxy A- and M-series phones are yet to receive the patch. Until that happens, you can turn off Wi-Fi calling and VoLTE on the phone. Here's how.
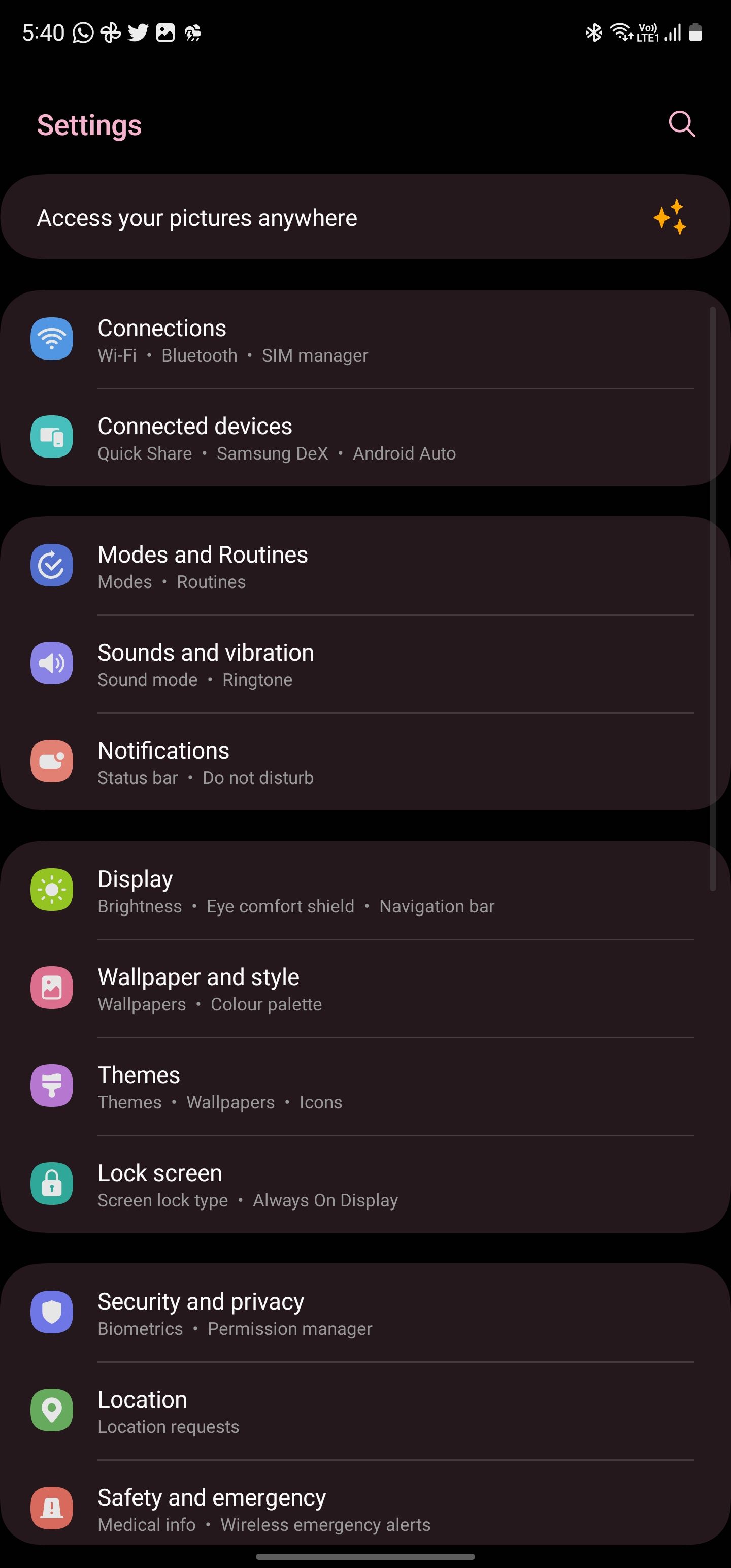
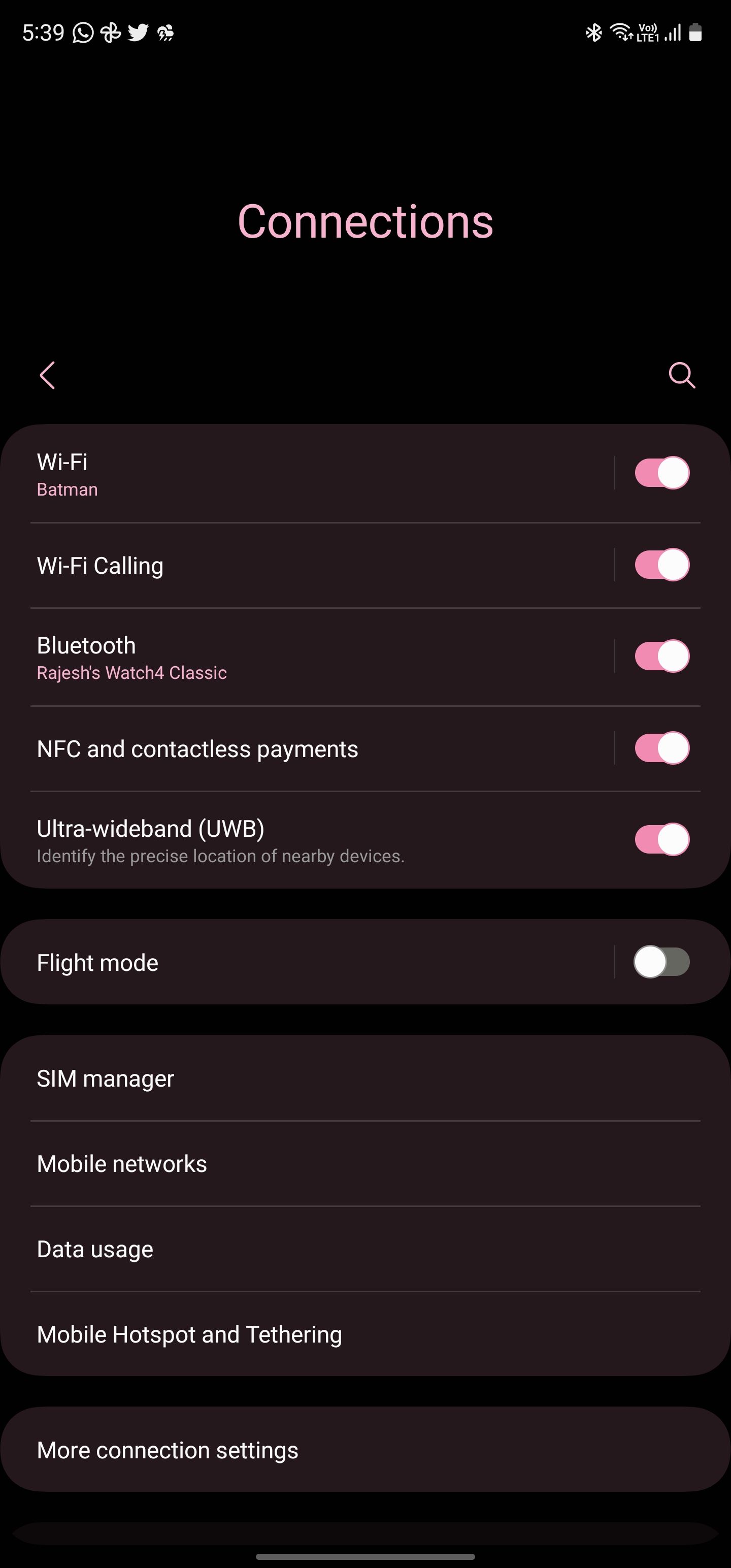
- Navigate to Settings -> Connections on your Samsung phone.
-
Disable the Wi-Fi Calling toggle from the menu.
Like Pixels, Samsung does not provide a toggle to disable VoLTE on its phones. You can work around this limitation by switching your phone to 2G/3G-only mode from Settings -> Connections -> Mobile networks -> Network mode.
While it might seem like Samsung has done a better job than Google at patching the Exynos modem vulnerability, that's seemingly not the case. As Project Zero security researcher Maddie Stone notes in a tweet, the exploits were revealed to Samsung at least 90 days before the report was published. And yet, not all the affected Galaxy phones have received the update at the time of writing. To be fair, Google had far fewer devices to patch, but that's hardly a consolation for people left with vulnerable phones.
What about Vivo phones?
If you own any Vivo phone affected by the vulnerabilities, your only option is to disable VoLTE and Wi-Fi calling until the company rolls out a fix. Unlike Samsung and Google, Vivo is not known for its speedy software updates. Plus, all the affected devices are old, so it is unclear whether the company will even roll out the March 2023 patch.
What if your car uses the affected Exynos chipset?
Sadly, you can't do much if your car uses the Exynos Auto T5123 chipset. Unlike phones, you can't simply disable Wi-Fi calling and VoLTE and call it a day. But on the bright side, it is harder to remotely hack into your car's Exynos modem since its number is not easily known.
Samsung is likely working with affected vehicle manufacturers on rolling out a fix for the Exynos modem vulnerability. But there's no clarity on when this will happen. Most cars automatically install an update in the background, so you won't know when the exploit has been patched.
Provided the option exists in your car's infotainment system, you can disable mobile connectivity entirely for a few weeks. This should hopefully be enough for Samsung and your car's manufacturer to patch the exploit. Until then though, you won't be able to enjoy any of the remote features of your vehicle.



