Almost anyone in the tech industry already recommends and uses password managers to create unique and hard-to-crack passwords. The vast majority of people are still reusing too many passwords for too many services. On top of that, passwords themselves can be insecure when not properly protected by online services. To combat this, Google has added support for passkeys to Chrome 108, an alternative to passwords.
According to Google, passkeys are supposed to address the aforementioned shortcomings with passwords. Passkeys can’t be reused for different services, Can't be leaked as part of server breaches, and they can’t be phished from unsuspecting users. Passkeys also aren’t exclusive to Google, which makes them versatile and cross-platform compatible. They can be used on different operating systems and work with different browsers and a handful of password managers like 1Password, though many others have already pledged that they will add support.
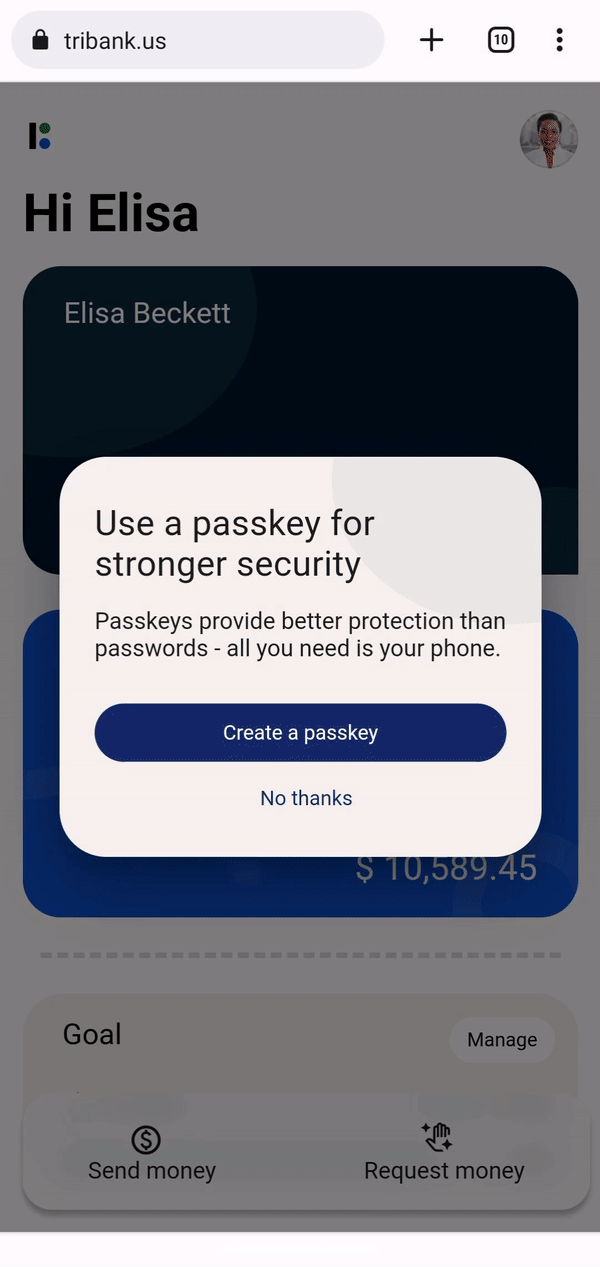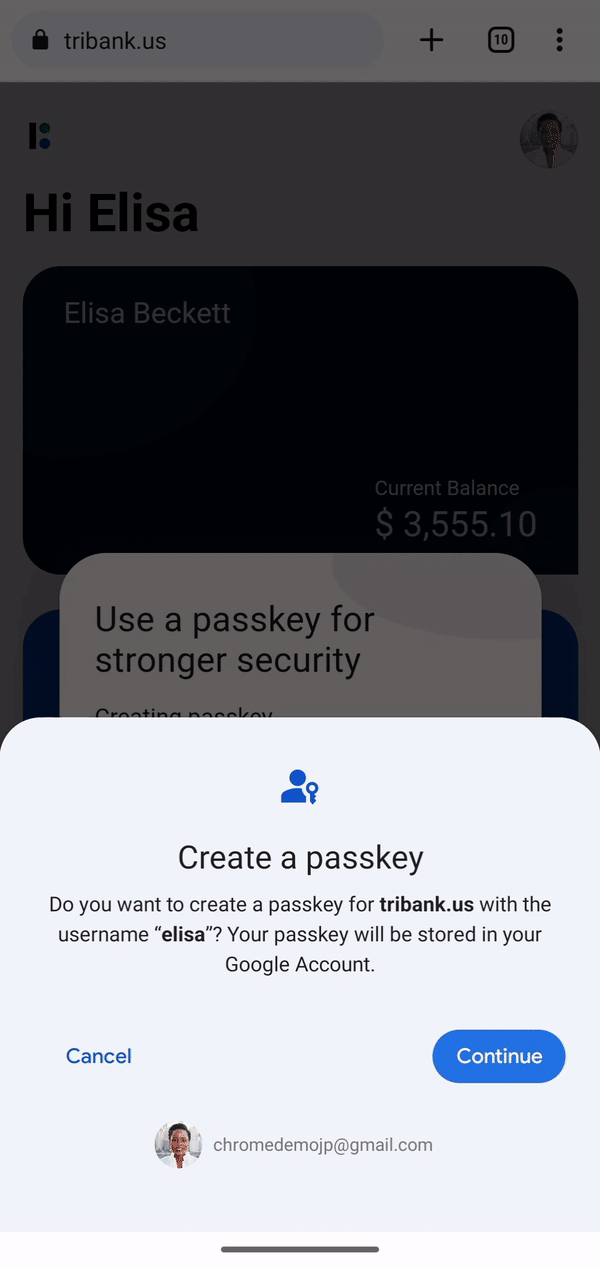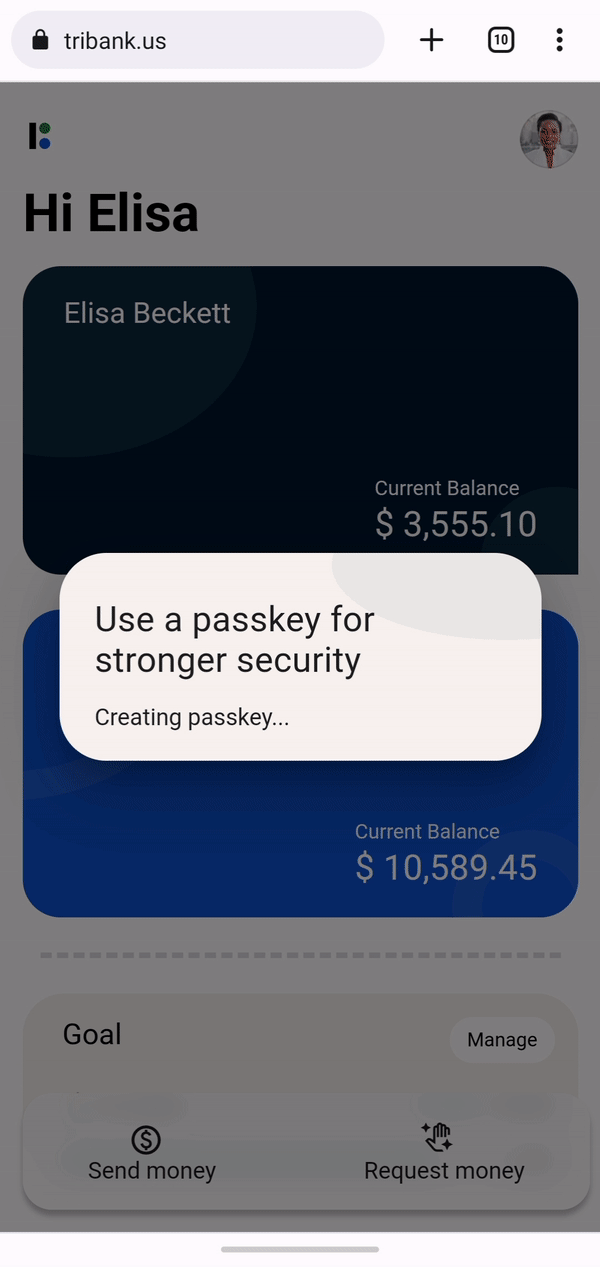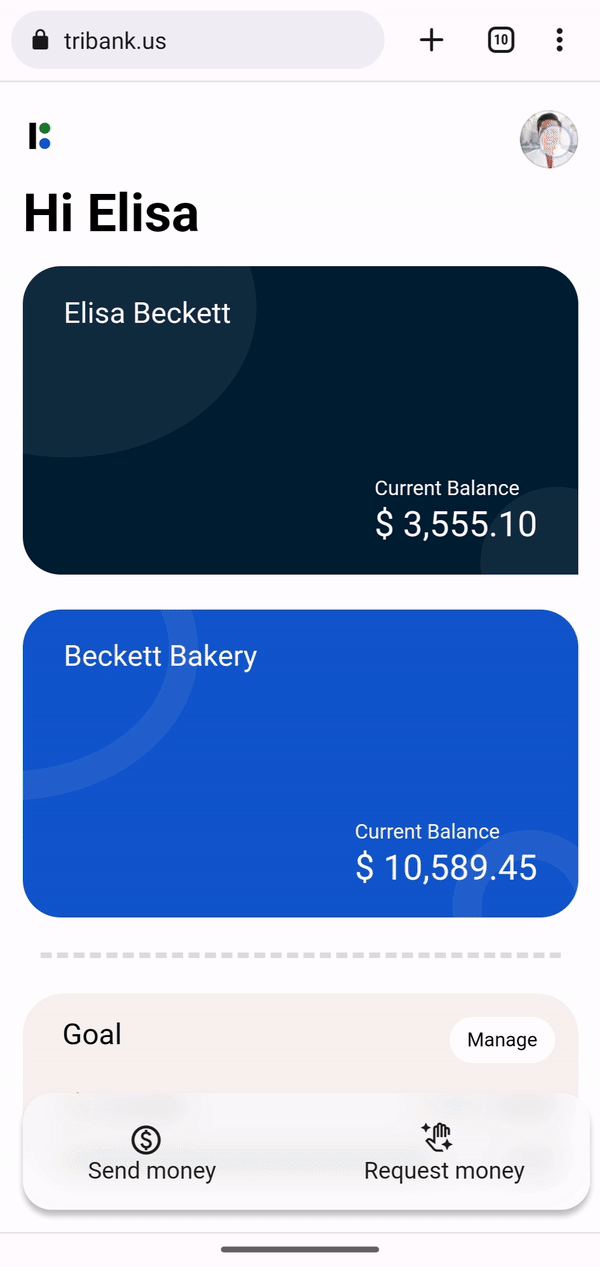
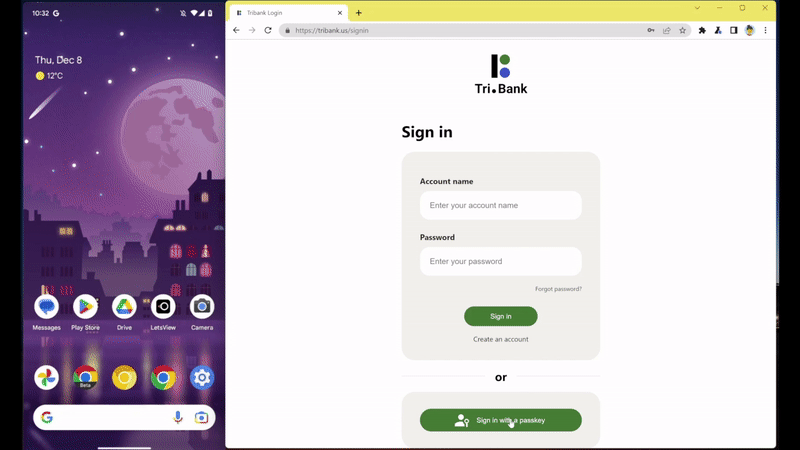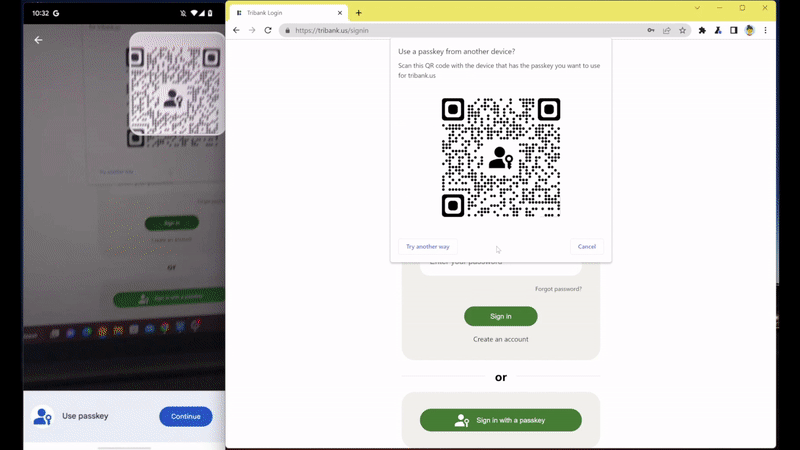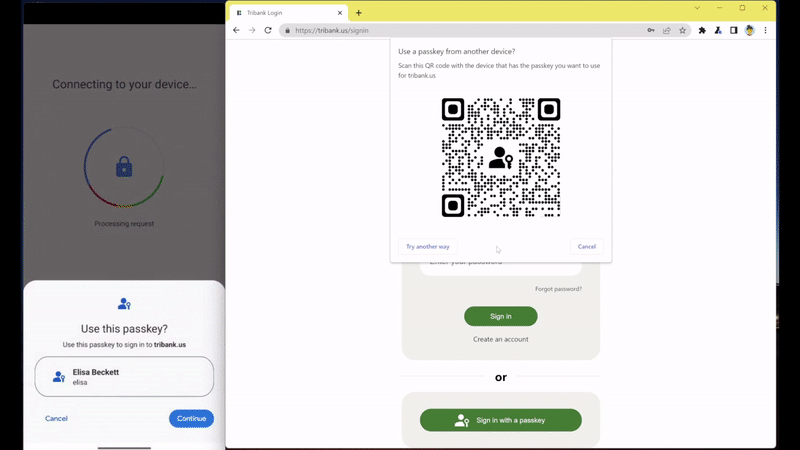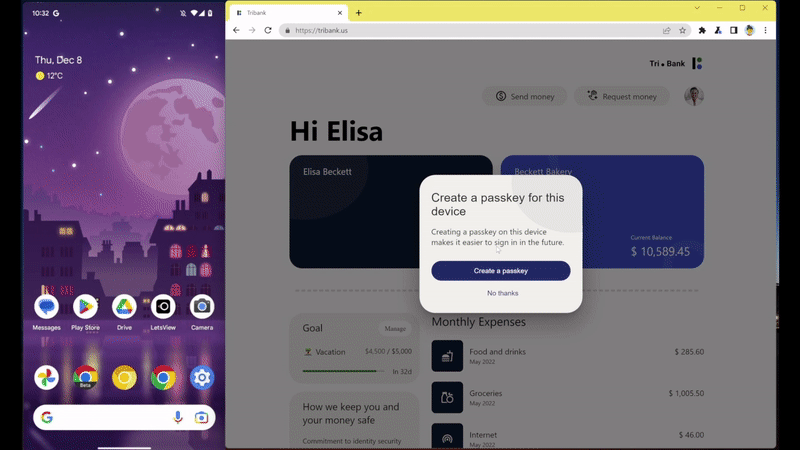
After a few months of testing, passkeys are now available in Chrome for Android, macOS, and Windows 11 on websites and apps that have implemented support for them. On Chrome, passkeys will be synced and saved to the Google Password Manager. When you sign up for an account with a website that supports passkeys, you will be prompted to create a passkey and then verify with your screen lock or fingerprint. Once it’s saved, you can then log in with Google Password Manager’s autofill, just like you would for any password-based service. The difference is just that you don’t have an actual password that you could type out or that could leak.
If you want to sign in from a device where you’re not logged in, such as Chrome for desktop on someone else’s computer, you will still need your phone to log in with a passkey. You need to scan a QR code in order to authenticate yourself. In the process, your passkey itself is not transferred to the computer.
When it comes to syncing passkeys across your own devices, Google only ever uploads end-to-end-encrypted copies of the passkeys to its password manager. To get access to them, you need to authenticate yourself with one of your own devices, preventing Google or a bad actor inside Google from ever getting their hands on your passkeys. To authenticate yourself with passkeys, you will also always need to unlock your device’s lock screen, and brute-force attacks are thwarted after a maximum of 10 false attempts, making it near impossible to impersonate you. To recover access for the legitimate owner, Google has a number of fallbacks up its sleeve the company describes in its security blog.