Pixel owners have suffered editing their screenshots using the default markup tool. The paint inputs aren't great at redacting anything, even if you scrub a spot real hard, and the crop tool is hilariously lacking any preset aspect ratios. But there's another reason why you shouldn't use markup and it's the reason why you might want to take a look at where or who you've sent your images to.
Researchers Simon Aarons and David Buchanan have gone public with an exploit they are dubbing "aCropalypse" which, in essence, allows anyone to take a PNG screenshot cropped in Android's default markup tool and undo at least some of the edits to produce portions of the image that were not intended for viewing. While the exploit was reported to Google and is patched in the March security update for Pixels (see CVE-2023-21036), redacted images sent on certain platforms — including, but not limited to Discord prior to mid-January — through the last several years could be at risk of being exposed.
You can see the exploit in action with your own images by using this demonstration tool provided by the aCropalypse researchers. We've also been given further information about the discovery and patching of this exploit by the researchers in advance of its publication to this webpage.
What's wrong, the human friendly version
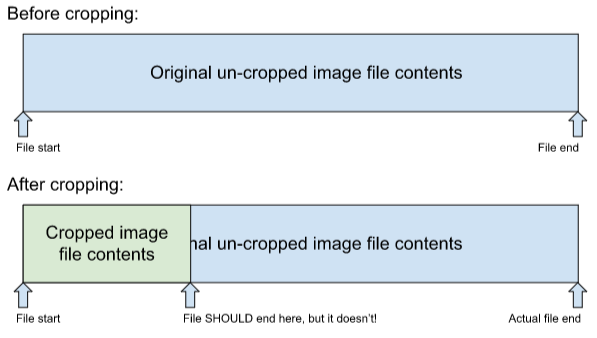
The technical aspects of the exploit seem to stem from a change to an API in Android 10 (see this IssueTracker thread from 2021 and a general explanation from Redditor OatmealDome). Prior to the change, an app tasked with writing new data to an existing file would truncate said file by default if the amount of that new data was less than what the original file held. With the change, that truncation behavior was no longer default.
So, if the amount of new data was less than what the existing file held, because data-writing occurs sequentially, the back end of the existing file would stay on, intact, as part of the new file. This change presented some negative outcomes: if the old data was unnecessary to the new file, it'd at least be taking up precious storage space; if the data was of a sensitive nature, those with the right tools could read and extract it on its own for malicious uses.
While the issue was eventually deemed to be "fixed" — as far as we can tell, guidance has changed on the write mode apps should use — the markup tool still used this untruncated write mode.
Aarons consulted Buchanan on this vulnerability with regards to PNG screenshots (not JPEGs) on January 2 and Buchanan was able to quickly develop a proof of concept for the current exploit. The two informed Google of the bug that same day. The company acknowledged the bug on January 3. A fix was internally finalized on January 24, but it did not begin going out to Pixel devices until March 13 with the month's security patch.
The engineer has posted to his personal blog about the actual goings-on, but from a high-level perspective, here's what's happening: PNG as a file format compresses data through certain processes over a series of blocks. Any given block of compressed data may contain references to the previous block of data, theoretically paving the way for previous blocks of data to be decompressed one by one. Thus, Buchanan was able to develop a decompression method that combines that look-back aspect with some cryptographic detective work focused on the intact, carried-over file data to gain context on what should be revealed.
Impact
As you know by now, the result is that an image edited in the markup tool can have portions of the original, unedited image after the fact with some know-how. In addition to Pixels, certain non-Pixel Android devices and custom ROMs also use markup.
While most online platforms will perform their own processing (such as further compression or stripping metadata) on user-uploaded images, Discord had not been processing image uploads adequately to prevent this exploit from working. aCropalypse researchers say the instant chat app began stripping trailing data from files on January 17. But this means markup-edited images dating as far back as late 2019 could be uncompressed to reveal information not intended for public viewing.
While Discord does have rich search tools to help users find image files they may have shared, you may have a lot of non-screenshot content to sift through and not every screenshot you've sent may be exploitable — we tested a screenshot on a Pixel 6a against the demo tool and couldn't get a result, but we've noted other users who have reported workable findings online.
Buchanan said in his blog post that he wrote a script to scrape his Discord uploads for any vulnerable images and found "lots of them." While most were generally harmless, he did have a screenshot of an eBay order and was able to extract his full postal address from it.