If you were disappointed to hear that Android 13 wouldn't support DNS over HTTPS, I've got some good news. It turns out that Google wasn't going to deploy it as part of a major Android update because (as noted at the time) it could also actually be implemented through a separate Android Mainline/APEX module, which would bring the feature to even more Android hardware, and that's exactly what has happened. Flying in the face of "fragmentation," Google just brought DNS over HTTPS to all Android 11 devices and later, and even some Android 10 devices.
Google announced the feature today on its Security Blog, explaining the benefits (if you weren't already aware of them) as well as the mechanism for how the change has rolled out. If you weren't aware of it, DNS over HTTPS offers some big advantages to your security.
What is DNS over HTTPS?
While you might already be aware of things like HTTPS connections as being a more secure way to browse the internet (thankfully, the default experience almost all the time now), there's actually still a gap in security that happens when you actually navigate to a new site. See, when you visit a web address, you aren't connecting to a string of words. That's not a real address, just an abstraction for the true location you need to connect to — the "domain name" is tied to an IP address.
Fundamentally, when you type androidpolice.com into your address bar, you're looking up that name in a sort of phone book — that's the DNS system. And, it turns out, DNS queries aren't actually done in a secure method by default, exposing you to things like man-in-the-middle attacks where someone can point you at the wrong place when you ask for an address. There are ways to plug the gaps in security even with this relatively insecure query, but the system still has a "bootstrapping problem," where the chain of trust in any order of operations becomes difficult to establish.
Making these queries in an unencrypted way is also a privacy concern, as someone in the right position could see which sites you're visiting or potentially even interfere with accessing certain ones. Remember back when ISPs used to route domains that didn't resolve to their homepage or ads? This should prevent that, and it can also make a dent against regulatory attempts to block traffic to certain sources, like the UK government's repeated attempts to block adult content.
Android has already supported one method of using DNS over TLS to fix this issue, allowing you to have an encrypted query to a DNS server — and that means you can trust the address that's provided when you ask, assuming you trust the server. That has some benefits and drawbacks. Some companies like Cloudflare have argued that it's slightly less secure since it can't fully disguise DNS queries as regular HTTPS traffic. On top of that, DNS over HTTPS delivers performance improvements and has already been adopted by a lot of DNS operators (including Cloudflare and Google). According to Google's John Wu (the developer originally behind the popular Magisk root solution) the implementation here is even written in Rust — something both security-mindful programmers and Rust enthusiasts will dig.
Now here for Android 11 and later
As mentioned, the feature has been implemented as part of Android's DNS Resolver module, and an update for it has rolled out as part of a recent Google Play system update. According to Google, compatible devices should already support it. While this module was optional in Android 10, according to Esper.io's Mishaal Rahman, it became mandatory in Android 11, so all Google-certified Android 11 devices and later that receive Google Play system updates should be able to use it, and some Android 10 devices that implemented the feature when it was optional may also have it. According to Rahman, it's easy to test by running "cmd device_config get netd_native doh" in an ADB shell (no quotes. If it returns "1," you've got DNS over HTTPS.
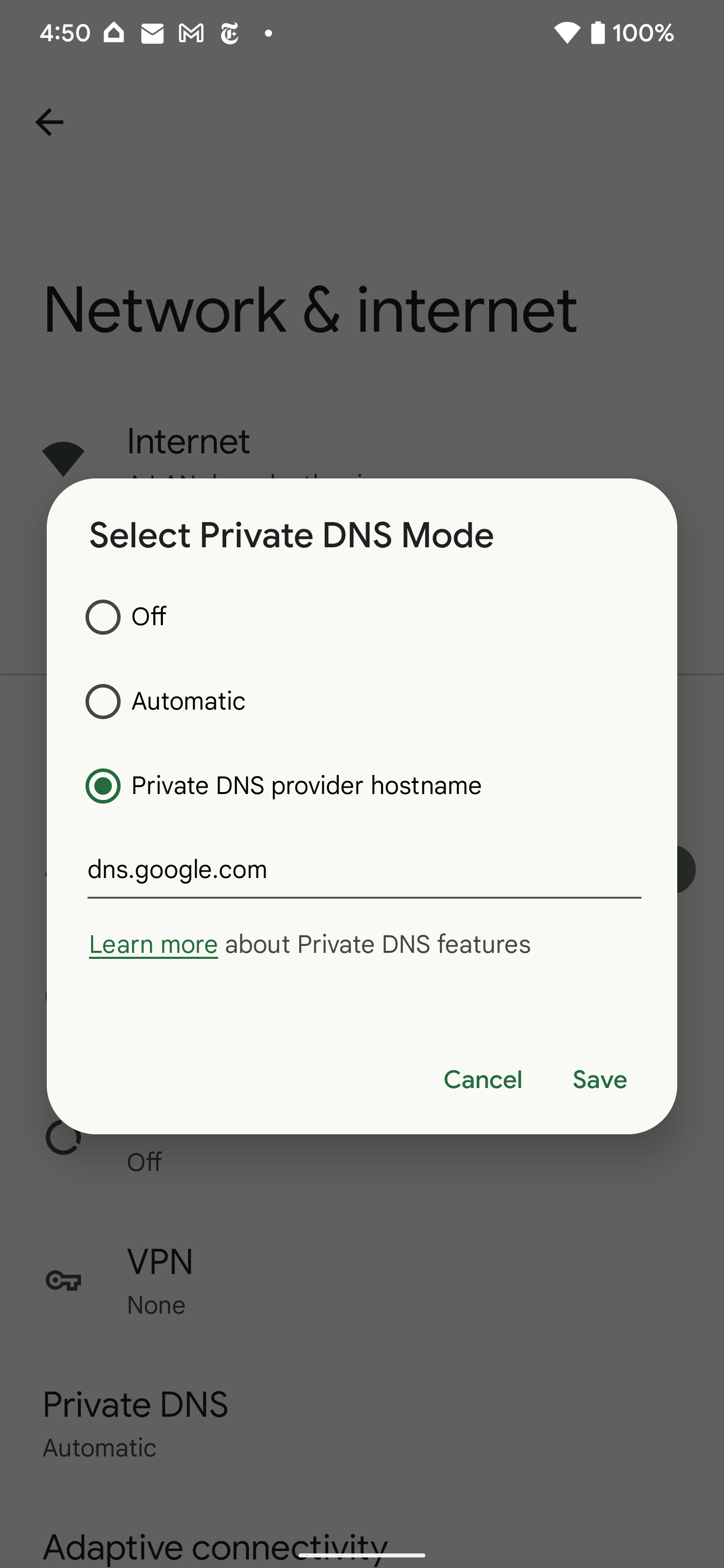
If all of this went over your head, the very short version is that Google was able to give the probable vast majority of Android devices in the wild a feature that will let them use the internet even more securely and safely. The feature may not provide many benefits, though, if your DNS server isn't compatible with DNS over HTTPS, but you can forcibly enable your Android device to connect to one by enabling the Secure Private DNS feature (search for "Private DNS" in Settings) selecting "private DNS provider name" and providing either Google or Cloudflare's hostnames.
- Cloudflare: cloudflare-dns.com
- Google: dns.google
(If you try a more targeted hostname like 1dot1dot1dot1.cloudflare-dns.com, that doesn't work for some reason.)
Eventually, this upgraded system should just work without you having to even worry about which DNS server you might be using. For now, the feature is ready; it's on DNS providers to finish rolling out support for DNS over HTTPS.