Read update
- Google attributes the change to potential geotag hijacking
Android may have started with the mantra that developers are allowed to do anything as long as they can code it, but things have changed over the years as security and privacy became higher priorities. Every major update over the last decade has shuttered features or added restrictions in the name of protecting users, but some sacrifices may not have been entirely necessary. Another Android 11 trade-off has emerged, this time taking away the ability for users to select third-party camera apps to take pictures or videos on behalf of other apps, forcing users to rely only on the built-in camera app.
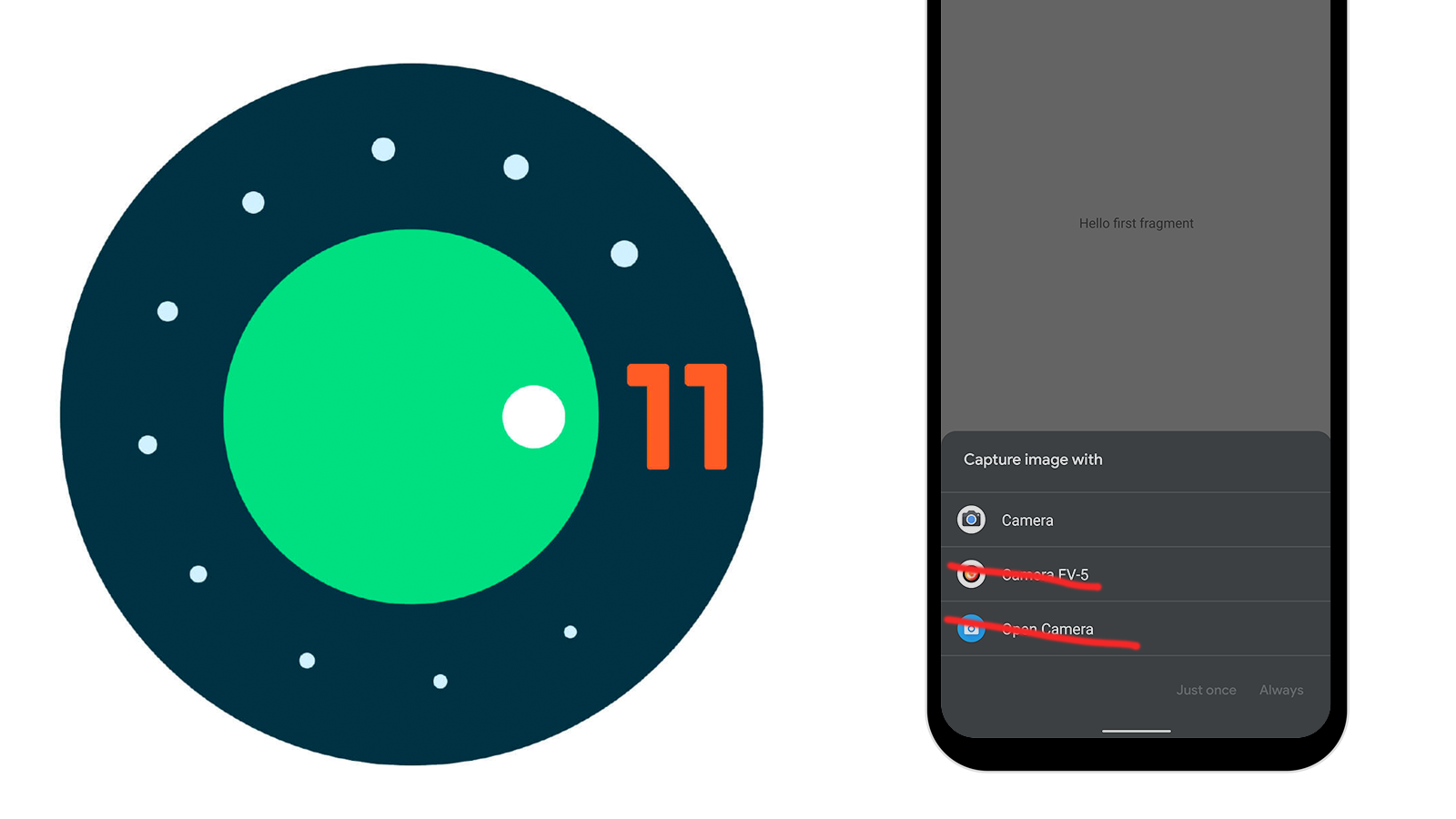
At the heart of this change is one of the defining traits of Android: the Intent system. Let's say you need to take a picture of a novelty coffee mug to sell through an auction app. Since the auction app wasn't built for photography, the developer chose to leave that up to a proper camera app. This where the Intent system comes into play. Developers simply create a request with a few criteria and Android will prompt users to pick from a list of installed apps to do the job.
Camera picker on Android 10.
However, things are going to change with Android 11 for apps that ask for photos or videos. Three specific intents will cease to work like they used to, including: VIDEO_CAPTURE, IMAGE_CAPTURE, and IMAGE_CAPTURE_SECURE. Android 11 will now automatically provide the pre-installed camera app to perform these actions without ever searching for other apps to fill the role.
Starting in Android 11, only pre-installed system camera apps can respond to the following intent actions:
android.media.action.VIDEO_CAPTUREandroid.media.action.IMAGE_CAPTUREandroid.media.action.IMAGE_CAPTURE_SECUREIf more than one pre-installed system camera app is available, the system presents a dialog for the user to select an app. If you want your app to use a specific third-party camera app to capture images or videos on its behalf, you can make these intents explicit by setting a package name or component for the intent.
Google describes the change in a list of new behaviors in Android 11, and further confirmed it in the Issue Tracker. Privacy and security are cited as the reason, but there's no discussion about what exactly made those intents dangerous. Perhaps some users were tricked into setting a malicious camera app as the default and then using it to capture things that should have remained private.
"... we believe it's the right trade-off to protect the privacy and security of our users." — Google Issue Tracker.
Not only does Android 11 take the liberty of automatically launching the pre-installed camera app when requested, it also prevents app developers from conveniently providing their own interface to simulate the same functionality. I ran a test with some simple code to query for the camera apps on a phone, then ran it on devices running Android 10 and 11 with the same set of camera apps installed. Android 10 gave back a full set of apps, but Android 11 reported nothing, not even Google's own pre-installed Camera app.
Above: Debugger view on Android 10. Below: Same view on Android 11.
As Mark Murphy of CommonsWare points out, Google does prescribe a workaround for developers, although it's not very useful. The documentation advises explicitly checking for installed camera apps by their package names — meaning developers would have to pick preferred apps up front — and sending users to those apps directly. Of course, there are other ways to get options without identifying all package names, like getting a list of all apps and then manually searching for intent filters, but this seems like an over-complication.
The new behavior is enforced in at least the current Android 11 beta release, and it will happen to any apps regardless of whether they target API 30 or something lower. We don't know yet if the Android CTS (Compatibility Test Suite) will require this behavior or if OEMs will be allowed to change it back to the previous rules, but it's likely this will become the standard going forward.
This certainly isn't a devastating change, and for many users that already default to their built-in camera, it will be entirely transparent. And most apps will still allow users to switch over to their preferred camera to grab a good shot, then upload it from the gallery. However, this means more work for users, and it's a kick in the pants to people that regularly snap profile pictures with a filter or for those that rely on G Cam ports to replace their stock camera. Additionally, some apps don't allow for different workflows, meaning you're stuck with whatever camera app is there.
UPDATE: 2020/08/20 2:11PM PDT BY CODY TOOMBS
Google attributes the change to potential geotag hijacking
In a response to The Verge, Google explained that this change was made to "keep bad actors from potentially harvesting your location." This explanation was also added in an update to the list of changes in Android 11, along with more technical details and a clarification that this does not inhibit the ability to install and use third-party camera apps.
This is designed to ensure that the EXIF location metadata is correctly processed based on the location permissions defined within the app sending the intent.
To receive EXIF location metadata from the pre-installed system camera app when using intents that have one of the preceding intent actions, your app must declare
ACCESS_MEDIA_LOCATIONin addition to theACCESS_COARSE_LOCATIONorACCESS_FINE_LOCATIONpermission.If you want a specific third-party camera app to handle your app's intent, you may do so by explicitly specifying the third-party camera app’s package name to fulfill the intent.
This change does not affect users' capability to install and use any camera app to capture images or videos directly. A user can set a third party camera app as the default camera app. This change also doesn't affect intent actions that launch the user-specified default camera app, including
android.provider.MediaStore.INTENT_ACTION_STILL_IMAGE_CAMERA,android.provider.MediaStore.INTENT_ACTION_STILL_IMAGE_CAMERA_SECURE, orandroid.provider.MediaStore.INTENT_ACTION_VIDEO_CAMERA.
Harvesting EXIF data in this way has actually been documented in the past when Shutterfly was caught doing it in 2019. This change will restrict the easiest path to hijacking location data, but it leaves some workarounds like calling out to camera apps directly or asking users to take photos and load them from a media provider. It's possible Google may have to take additional steps to completely shut the door on this tactic.