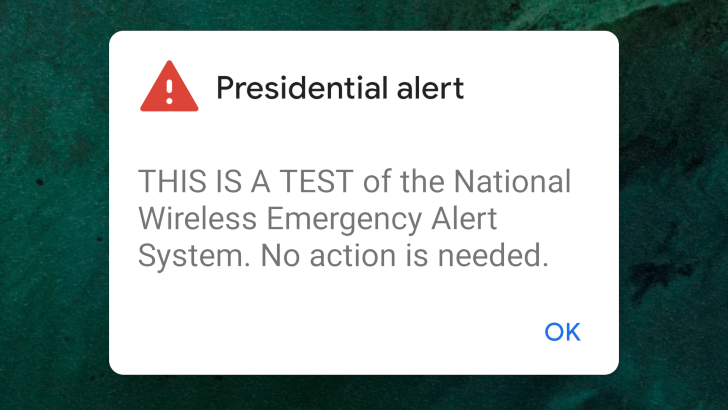
Last year, the United States performed the first public test of the national Wireless Emergency Alert (WEA), an alert system designed to send messages to smartphones, TVs, and other systems simultaneously. The test was specifically for the 'Presidential Alert,' a new category that can't be opted out of (like AMBER alerts). It turns out these types of alerts can be easily spoofed, thanks to various security vulnerabilities with LTE towers.
A group of researchers at the University of Colorado Boulder released a paper that details how Presidential Alerts can be faked. An attack using a commercially-available radio and various open-source software tools can create an alert with a custom message. Researchers were able to use just four malicious portable stations to cover a 50,000 seat stadium with a 90% success rate:
Our attack can be performed using a commercially-available software defined radio, and our modifications to the open source NextEPC and srsLTE software libraries. We find that with only four malicious portable base stations of a single Watt of transmit power each, almost all of a 50,000-seat stadium can be attacked with a 90% success rate. The true impact of such an attack would of course depend on the density of cell phones in range; fake alerts in crowded cities or stadiums could potentially result in cascades of panic.
The attack is possible thanks to multiple vulnerabilities in how LTE works. First, alerts come from a specific LTE channel, so malicious alerts can be sent out once that channel is identified. Second, phones have no way of knowing if an alert is genuine or not. Adding digital signatures to alerts could potentially solve the latter problem, but the task would require device manufacturers, carriers, and government agencies to work together.
It's not great that the system designed to broadcast messages about life-threatening emergencies can be easily hijacked, but given all the other ways cell towers can be manipulated and spoofed, it's hardly surprising.
Source: ACM
Via: TechCrunch