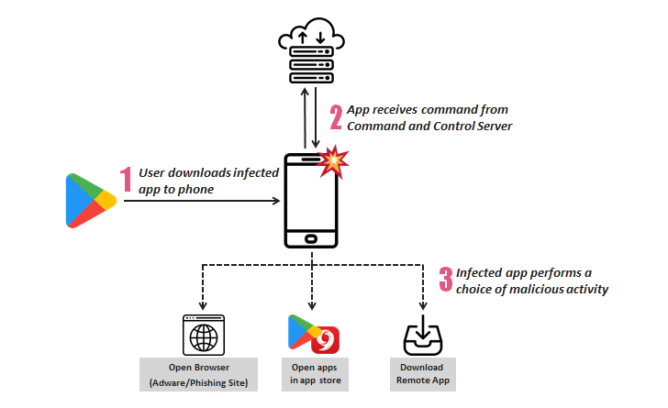
Another day, another security problem. This time, we have what's been dubbed SimBad by the Check Point research team, a rogue adware campaign found to affect over 200 now-removed apps in the Play Store — these apps together accounted for over 150 million downloads. It shows out-of-context ads, exposes users to other malicious apps, and can even open a URL in the browser without the user's consent.
Found in the "RXDrioder" ad-related SDK, the researchers do not believe the creators of the SDK were aware of the malicious elements and were rather scammed into using the SimBad code. It was named SimBad due to the fact that it was mostly found in simulator games.
According to the report, SimBad has three malicious capabilities: showing ads, phishing, and exposure to other applications. It can open a URL in the device's browser which leads to a variety of phishing attacks, or it can search for specific apps in the Play Store or other app stores, further increasing the security risks on the user's phone. Someone using SimBad can even install a remote app, which allows for installation of further malware.
Check Point informed Google about SimBad, which resulted in the 206 affected apps being removed from the Play Store entirely. The researchers warn that SimBad is just adware right now, but it has the structure and potential to grow into something much worse. Hopefully, their efforts and Google's actions have stopped it from getting out of hand.
Source: Check Point