Recently, Google has notified developers of apps that use Accessibility features for purposes other than helping users with disabilities to cease using those APIs or otherwise unpublish their app. The impetus for this move appears to be existence of (now removed) apps in the Play Store which use Accessibility features in conjunction with a vulnerability patched as part of the September security update to install malware.
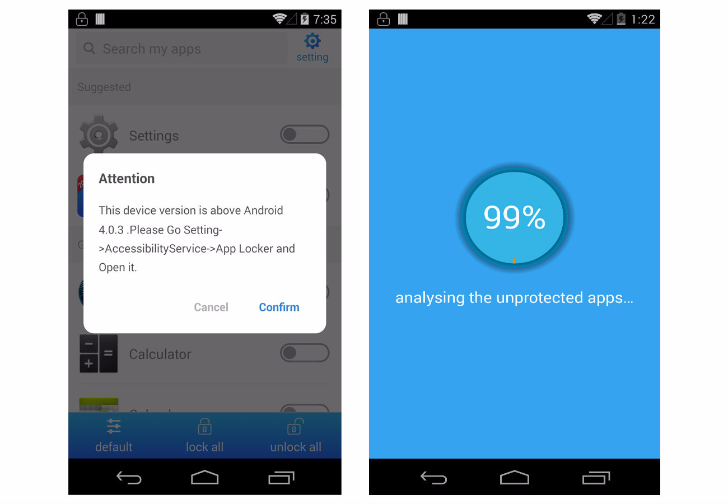
The report from security software vendor Trend Micro identified various malicious apps titled "Smart AppLocker," one of which the company claims had over 500,000 installs. These apps used Toast notifications to display a fake progress bar for an app which purports to restrict other apps from running without the user inputting a PIN. On first use, the app reports that it requires Accessibility permissions to operate. When these permissions are granted, a full-screen Toast notification is used to cloak the actual screen contents.
As the screen contents are being cloaked, the app enables installation of apps from third-party sources, force stops security apps, downloads and installs a second APK, and grants that app accessibility permissions. The malicious app and malware payload, dubbed TOASTAMIGO and AMIGOCLICKER by Trend Micro, are the first apparent instances of exploits of this vulnerability in the wild.
The apps cited by Trend Micro have been removed from the Play Store. Although the underlying vulnerability, CVE-2017-0752, was patched in AOSP for 4.4.4, 5.0.2, 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1, and 7.1.2, actually receiving the update requires your device manufacturer to push a software update, or installing a custom ROM which properly integrates the latest security patches from AOSP. You can also go check which apps you've granted accessibility access to and whether you trust them or not.
Source: Trend Micro