About nine months ago, Rootjunky managed to bypass the factory reset protection (FRP) on Samsung devices simply by inserting an OTG drive into the phone and installing an app. Then, two months later, he found a vulnerability on LG phones; this time, he circumvented FRP by using talkback settings to open a browser, downloading an APK that opened settings, adding a new user, switching back to the main account, and then resetting without FRP. However, this new exploit for Samsung phones might be the most ingenious yet.
Factory reset protection was added to Android with 5.1 Lollipop, but since different OEMs use different variations of Android, vulnerabilities can arise. This particular method should work on recent Samsung devices like the Galaxy S6, S6 edge, S6 active, S6 edge+, Note5, S7, S7 edge, S7 active, and even the brand new Note7. It is entirely possible that it will work with other modern Samsung phones as well, though.
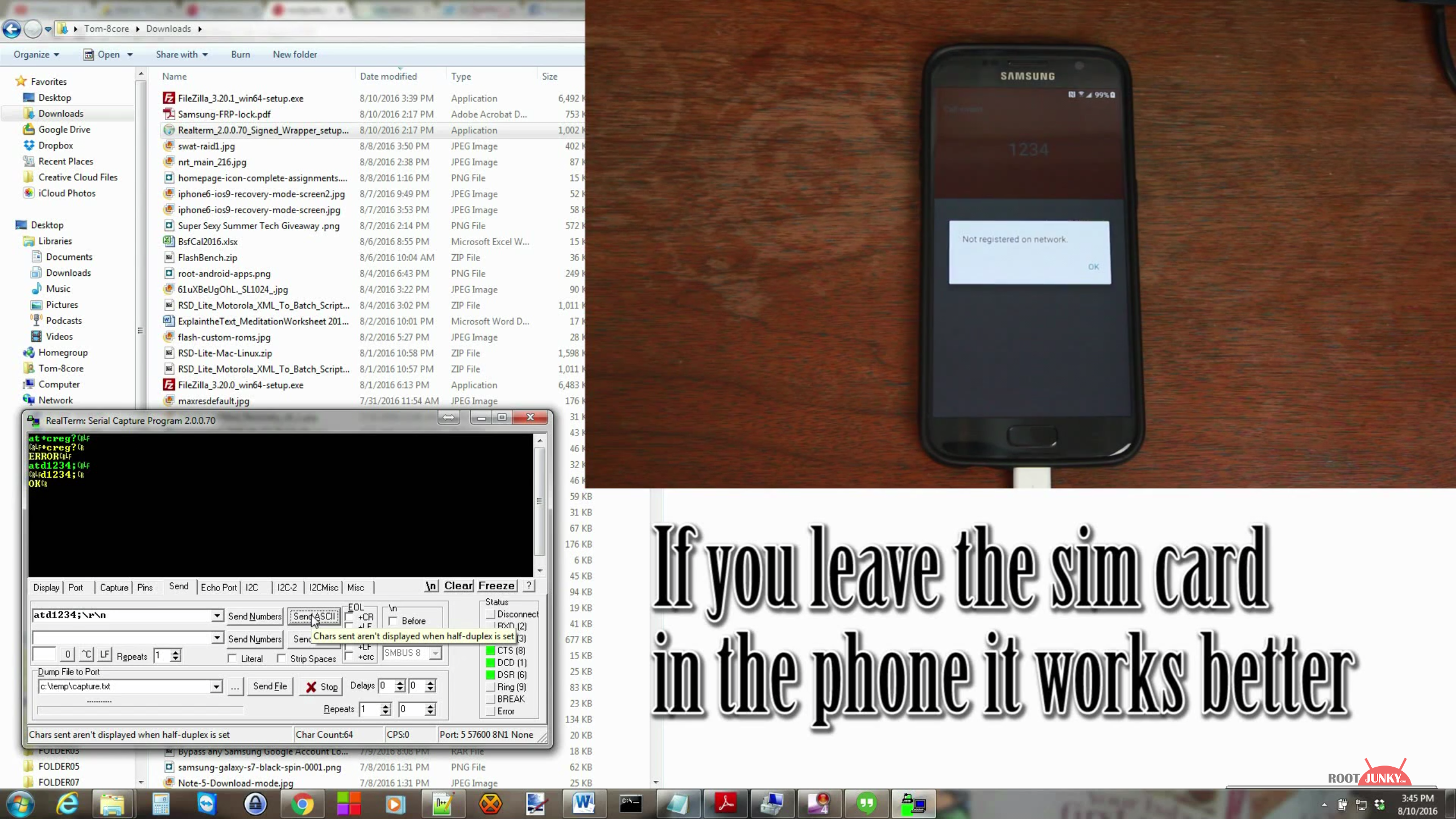
Rootjunky demonstrates the flaw with a T-Mobile Galaxy S7 on Android 6.0.1 with the July 1st security patch. After confirming that the FRP is activated in the bootloader, he reboots the phone, connects it to WiFi, then connects it to a computer. The next step is downloading a program from his site that allows him to send a fake call to the phone. Once the call comes in, he hits "Create contact", scrolls all the way down in the contact creation list, and clicks the "SCAN BUSINESS CARD" option. That opens a prompt to download the business card scanning app on Galaxy Apps. From there, it's a matter of downloading a file manager after signing into a Samsung account, which lets him get to an app he created that essentially acts as a shortcut to a Google sign-in screen. There, he hits the three-dot menu on the top right that permits him to open a web page to sign in through. After this, he signs into a new Google account, reboots the device, goes through the setup process once again, and voila! The S7 is able to be used normally again.
Factory reset protection is supposed to make stolen devices useless by preventing thieves from using them without the owner's Google account. However, it is sometimes unknowingly activated when people fail to remove their Google accounts prior to selling their phones. (A tip to sellers: don't change your password before resetting your phone.) Granted, Rootjunky's video could be used for evil, but for buyers in that situation, it will definitely come in handy.
You can find the full tutorial here. There's no guarantee it'll work on every Samsung device or every variant, but the fact that it works on any is still impressive.
Source: Rootjunky