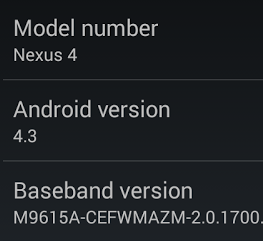
For the past few hours, I've been observing a curious case of Jeff Williams on Google+. Jeff posted a screenshot of what he claimed was a Nexus 4 he bought from a Googler... with a build of Android 4.3 on it. The same build, JWR66N, that we saw leaked earlier on a Galaxy S4 GPE by SamMobile.
In disbelief, some have called him a hoaxer, but a number of resourceful folks decided to get Jeff on IRC (channel #Android43 on freenode) and worked with him for hours, trying over and over to get the magical system dump that would prove Jeff's story to be real.
At 10:44PM Pacific, we finally had lift-off:
The system dump, which we have since confirmed as legitimate and along with dozens of other IRC members mirrored to multiple destinations, indeed belongs to a Nexus 4 (mako), and the build number is indeed JWR66N. The radio and bootloader are missing right now - Jeff promised them tomorrow - so I have my doubts about a working port to other Nexus 4s for the time being.
In the meantime, the system dump itself is ready to go, and Ron and I are ripping through it as we speak. We'll have a teardown ready for you soon if we do dig something up, and by the looks of things, there's enough for a post.
I'd like to thank Jeff for his persistence as well as IRC users efrant, gravufo, Jason__, vividboarder, Introspection, and everyone else who drove this one to the finish line.
Update: There's chatter on IRC that restoring the backup via TWRP recovery seems to work. I flashed my Nexus 4 using a flashable zip and have a quick guide on how to do this coming up shortly. It boots, and it works.
Update #2: One of the goodies inside the dump is a new Play Store v4.2.3. Go grab it.
Update #3: A quick video by Tristan Smith:
[EMBED_YT]https://www.youtube.com/watch?v=sIwNoeaBhnc
[/EMBED_YT]
Update #4: Here's how to update your Nexus 4 to Android 4.3 from this dump.
Download
I won't post links to Jeff's Dropbox because it'll blow through his bandwidth allocation in no time. Instead, here are several of our mirrors. The files inside are the system and boot (that's the kernel) partitions, tarred. Just untar them and have fun looking at the APKs: