latest
North Korean hackers targeted fintech and media with Chrome zero-day exploit
State-sponsored attackers went after targets with fake emails and spoofed websites
One of the more alarming terms in computer security is the "zero-day exploit." That label has some weight behind it for good reason, referring to a pretty scary situation where an attacker knows about a hidden major flaw or bug in some software — in this case a browser — for which there's not yet any fix available. Hackers love them, and now a new report from Google's Threat Analysis Group (TAG) outlines how a state-sponsored hacking gang based in North Korea has been exploiting just such a zero-day in Chrome.

Hackers funded by state money have been fighting battles online for years. With the ongoing Russian invasion of Ukraine, the cyber warfare front went from a simmer to a boil. While the combatants on the ground and in the air at the moment are primarily from two countries, reports from Google's Threat Analysis Group (TAG) indicate there are more players involved in cyberspace, including hackers working for China's military.

Nvidia and Samsung hackers take credit for Ubisoft attack
The game company says no personal info was exposed
Ubisoft may be the latest victim in a cybercrime spree that has already affected chipmaker Nvidia and South Korean electronics giant Samsung. As a result, the company had to take measures to reassure users that their info was safe. While Ubisoft didn't lay the blame on anyone, Lapsus$ — the cyber gang linked to the previous hits — seemed to take credit for this one as well.

In late February, the cyber gang calling itself Lapsus$ broke into Nvidia's internal network and managed to steal a lot of sensitive data, from hashed login credentials to critical trade secrets behind the company's chips. The hackers demanded Nvidia remove the lock on its newer GPUs that automatically slowed them down when mining cryptocurrency and was given until March 4 to comply — or Lapsus$ would release those trade secrets. The cybercriminals have started making good on their threats, and now the fallout from their data dump threatens to help malware avoid detection.

Samsung confirms massive hack, but says user data is safe
Hackers claim they have source code, encryption keys
Read update
The hacking group Lapsus$ recently targeted Nvidia, demanding the chipmaker eliminate a feature in some GPUs that limits hash rates while mining Ethereum cryptocurrency. The hackers made it clear they had the goods by first leaking internal Nvidia email handles and cryptographically hashed passwords, then setting a deadline of March 4. Lapsus$ isn't stopping there — now Samsung is under the gun, and valuable source code is once again at stake.
In the early days of Android, ES File Explorer was one of the better ways to manage your storage. That hasn't been true for a long time, though. Not only is the app rather cluttered and buggy, security researcher Elliot Alderson (@fs0c131y on Twitter) points out this app makes your files vulnerable to theft. All you have to do is open it once.
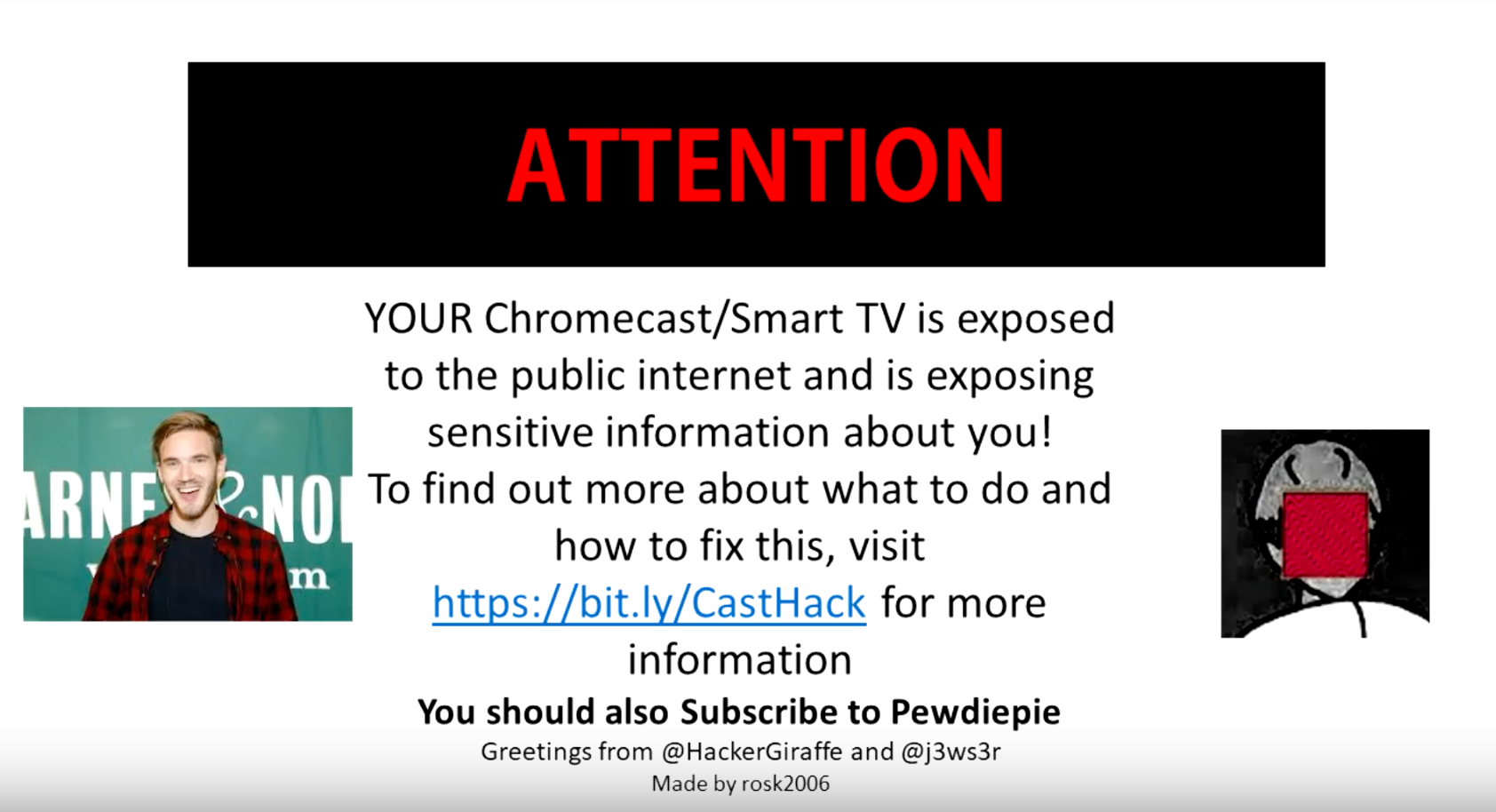
Read update
The internet-connected devices in our homes can make life more enjoyable, but they can also provide an in for internet ne'er-do-wells. A pair of jokers has undertaken a campaign of Chromecast hacking ostensibly to warn people about their vulnerability. Although, they're also promoting PewDiePie for some reason.

T-Mobile customers, your data has been put at risk by your carrier, once again. In what seems like copypasta at this point, a security researcher recently found a bug in a publicly discoverable subdomain on T-Mobile's website that gave anyone access to customer data using just a phone number. It's almost like T-Mobile wants to award those bug bounties.

In the words of a famous disc jockey: "Another one." A young hacker-turned-security researcher in England found a critical vulnerability on T-Mobile's website that basically left records of user logins exposed online for hackers to pillage. The bug was reported and patched in December, and T-Mobile says no customer information was compromised as a result of this flaw.

A security researcher has revealed that a recently patched hole in T-Mobile's security made it possible for hackers to vacuum up all your personal account information, and all they needed was your phone number. And you probably give that out all the time. T-Mobile says the vulnerability has been corrected, but there's some question as to how severe the data breach might have been.

We of a certain age remember the days before WiFi was widespread. It sucked. Now, there's a wireless network on every corner bringing you all the wonders (and horrors) of the internet. They can also bring you something else: hacks. A researcher from Google's Project Zero security team has revealed an exploit for Broadcom WiFi chips that can allow an attacker to execute code on your device. They just have to be on the same WiFi network as you.

The security of our mobile apps and private data is a very serious matter. This is particularly true for high value targets like web browsers, which often store login credentials that can be used to access many of the websites we use on a regular basis. Unfortunately, browsers are also very complicated applications with an extensive set of features that are difficult to lock down completely. Sebastián Guerrero Selma of viaForensics recently posted a video demonstrating a newly discovered vulnerability in Firefox for Android which would allow hackers to access both the contents of the SD card and the browser's private data. Take a look at the video:

That didn't take long. Just 2 days after Justin Case released a root method for the Moto X, Droid Ultra, Droid Mini, and Droid Maxx, he's already back with a hack that bypasses write protection. By disabling the write protection afforded by the bootloader, it becomes possible to flash 3rd-party ROMs, themes, and other mods. In other words, the flood gates are open for the modding community.

Apktool is a Windows/Mac/Linux utility for reverse engineering Android apps. It allows you to decode an app, change something, rebuild it, and pray it still runs. You're going to need something like this if you're into theming apps, hacking a feature onto someone else's app, finding security holes, or just want to hunt for info.

See All Your Purchased Android Apps In One Place With The Legacy Play Store
Since time immemorial, the Android Market app let you see a list of just your purchased apps under a "Not installed" section. When the Play Store change
Since time immemorial, the Android Market app let you see a list of just your purchased apps under a "Not installed" section. When the Play Store change happened, that list was still there. Then at some point with all the stealth updates, that list of paid apps went away. Thanks to Paul O'Brien over at Modaco, we have the Legacy Play app that solves that problem by bringing back the "Not installed" list.

[Update: Skyrocket, Too] Samsung Open Sources The Epic 4G Touch's Kernel Ahead Of Ice Cream Sandwich Update (FF18)
Today is a good day, I think, for source code drops! Samsung has just released the source code for an update for the Epic 4G Touch, Sprint's variant of
Today is a good day, I think, for source code drops! Samsung has just released the source code for an update for the Epic 4G Touch, Sprint's variant of the Galaxy S II. The update (FF18) is said to be rolling out to devices right now as an OTA. If you want to get your hands on the kernel code to fiddle with it yourself before the update arrives, however, you can head to Samsung's download page here.

Yesterday, we told you about the OpenGL video driver Chainfire3D. At the time, there was a common question: what can you really do with this? Some crafty XDA users have set out to prove exactly what you can do using CF3D, and here at AP, we all think it's nothing short of awesome.

Of all the things that are cool and impractical in this world, this has to be one of my favorites. At one point or another, all EVO 4G owners have wanted to ditch their desktop PCs in lieu of their smartphone, right? Okay, maybe not - but if you ever get the urge to do so, then XDA member Lokifish Marz has the setup for you.