An unusually advanced strain of malware was discovered on iOS last year, dubbed Pegasus by Lookout and other security firms that analyzed it. Now, an Android version of Pegasus has been discovered. The new malware is known as Chrysaor, and a full analysis of its origins and capabilities has been published by Google and Lookout. It's a serious piece of malware, but you don't have to worry about it showing up on your phone.
Chrysaor appears to come from the same "cyber arms dealer" that produced Pegasus, the Israel-based NSO Group. While the malware is incredibly sophisticated, it's targeted at older versions of Android—we're talking 4.3 Jelly Bean here. Additionally, it was never distributed in the Play Store. Instead, it appears to have been used for highly-targeted attacks on specific marks via sideloading.
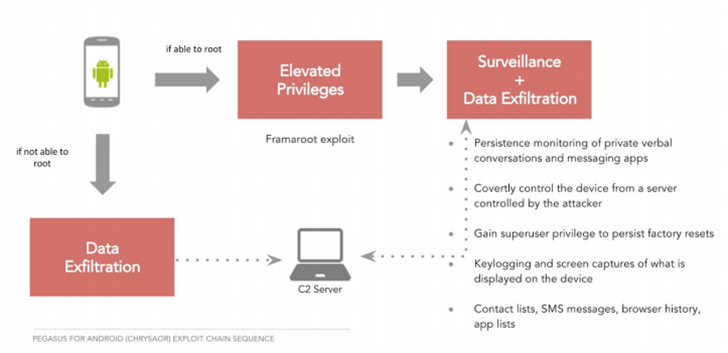
After getting the target to install the malware, it sets up shop using the Framaroot exploit. That exploit has been patched in modern versions of Android, though. If the system is not vulnerable to that tool, the malware can still operate in a reduced functionality mode to steal limited data. If Chrysaor successfully gains root, it installs itself on the /system partition to persist across factory resets. It will also disable the Samsung OTA service.
Chrysaor is controlled remotely with the intention of silently exfiltrating user data. It uses six tools to do so:
- Repeated commands: use alarms to periodically repeat actions on the device to expose data, including gathering location data.
- Data collectors: dump all existing content on the device into a queue. Data collectors are used in conjunction with repeated commands to collect user data including, SMS settings, SMS messages, Call logs, Browser History, Calendar, Contacts, Emails, and messages from selected messaging apps, including WhatsApp, Twitter, Facebook, Kakoa, Viber, and Skype by making /data/data directories of the apps world readable.
- Content observers: use Android's ContentObserver framework to gather changes in SMS, Calendar, Contacts, Cell info, Email, WhatsApp, Facebook, Twitter, Kakao, Viber, and Skype.
- Screenshots: captures an image of the current screen via the raw frame buffer.
-
Keylogging: record input events by hooking
IPCThreadState::Transactfrom/system/lib/libbinder.so, and intercepting android::parcel with the interfacecom.android.internal.view.IInputContext. - RoomTap: silently answers a telephone call and stays connected in the background, allowing the caller to hear conversations within the range of the phone's microphone. If the user unlocks their device, they will see a black screen while the app drops the call, resets call settings and prepares for the user to interact with the device normally.
The malware can be removed from a device in several ways. The command and control sever can issue an uninstall command, or the malware will simply self-destruct after 60 days of no sever access. The presence of an "antidote file" on the device's storage will also cause the malware to uninstall itself.
Google added the fingerprint for Chrysaor to the Verify Apps tool after being approached by Lookout. It reports seeing fewer than three dozen instances of the malware worldwide. Devices with Verify Apps enabled are now protected from Chrysaor, so you shouldn't have a problem even if someone were targeting you.